Secure Hard Drive Destruction for Your Business

Hitting "delete" on a file or reformatting a hard drive feels final, but the truth is your company’s sensitive data remains dangerously recoverable. For any organization, professional hard drive destruction is the only method that guarantees confidential information is permanently eliminated, protecting your business from a devastating and costly data breach. This isn't just about erasing files; it's about physically obliterating the storage media to make data recovery impossible.
Why Your "Deleted" Files Aren't Really Gone
Imagine this scenario: your company upgrades its office computers and sends the old ones off for what you believe is proper disposal. Months later, you receive the dreaded notification—a massive data breach. Your customer lists, proprietary financial records, and internal strategic documents are exposed. The source? A hard drive your IT team thought was wiped clean. This isn't a hypothetical threat; it's a common and incredibly costly operational failure.
The vulnerability lies in how operating systems handle "deletion." When an employee deletes a file, the system simply removes the pointer to that information and marks the space as "available for overwrite." The raw data remains on the drive's platters, easily recoverable with widely available software. Formatting a drive is equally insufficient, as it often just resets the file system while leaving the underlying data perfectly intact and accessible to forensic tools.
The Real Cost of Lingering Data
This residual data is a significant corporate liability. The entire secure shredding industry exists to mitigate this risk, driven by stringent privacy regulations and the staggering financial consequences of non-compliance. Recent reports show the average cost of a data breach has soared to USD 4.88 million. For financial services firms, that number is even higher, averaging USD 6.08 million. These figures underscore why professional, certified destruction isn't an IT expense—it's a critical investment in risk management.
For any business, viewing hard drive destruction as just another IT expense is a huge mistake. It’s a vital investment in risk management that protects your brand, your customers’ trust, and your ability to stay compliant.
From a Liability to a Recycled Resource
Proper destruction doesn't just solve a security problem; it addresses corporate environmental responsibility. Once a hard drive is shredded into tiny, confetti-like pieces, the raw materials like aluminum and other metals are separated and sent into the recycling stream. This secure process ensures your sensitive data is gone for good while giving the electronic components a second life. If you want to see what this looks like, you can learn more about what happens to recycled electronics.
Ultimately, secure data destruction provides a definitive, compliant end-of-life for an IT asset, ensuring it can never become a future risk to your organization.
Exploring Your Data Destruction Options
When an IT asset reaches its end-of-life, your organization must be absolutely certain the sensitive business data it contains is gone for good. However, not all data destruction methods are created equal. Understanding your options is the first step toward making a smart, secure, and compliant choice for your business.
Let's review the three main methodologies for data destruction. Think of them as different security tiers, each with its own ideal business use case—and significant limitations.
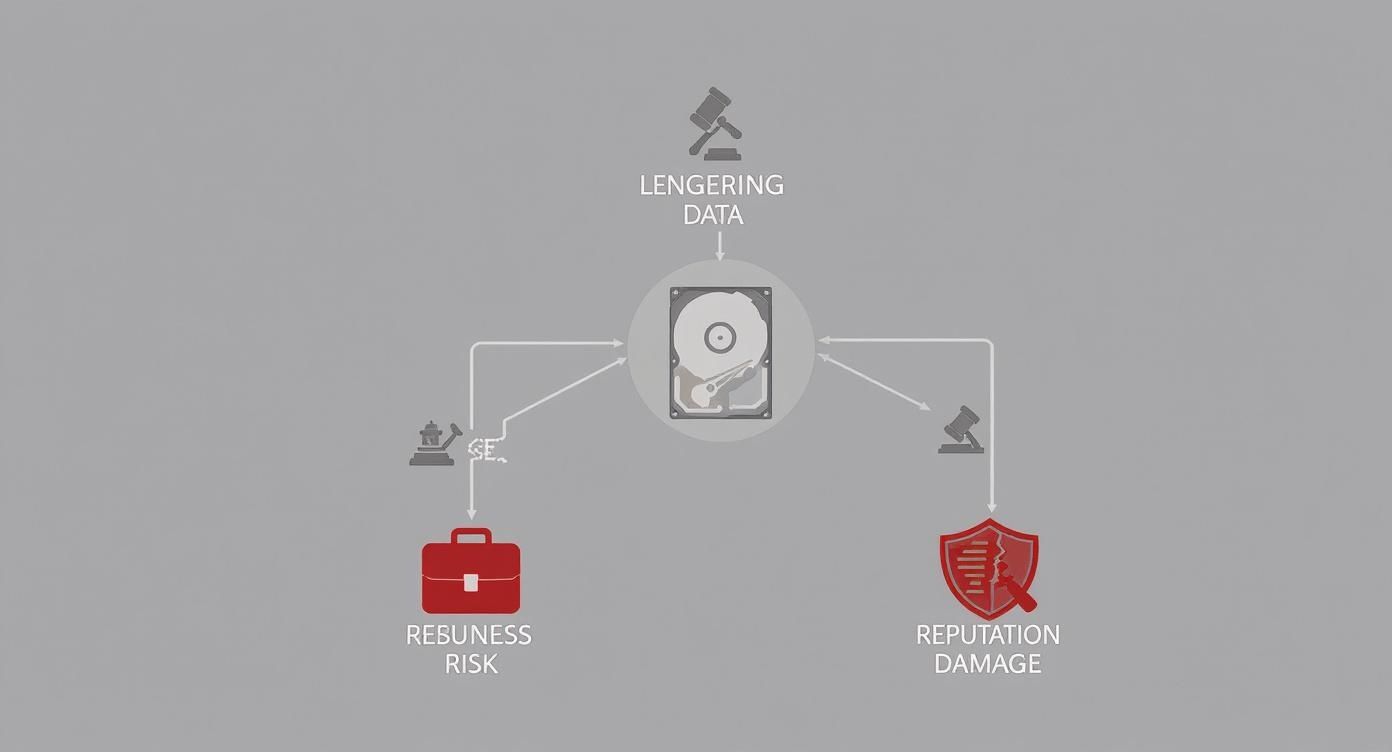
If you're wondering why this is so critical, this graphic lays it out pretty clearly. Lingering data isn't just a hypothetical problem; it's a direct line to serious business risks.
As you can see, failing to properly destroy data opens the door to financial, legal, and reputational nightmares that no business wants to face.
To help you choose the right path, we've put together a quick comparison of the three primary methods.
Comparison of Data Destruction Methods
| Method | Security Level | Best For | Key Weakness |
|---|---|---|---|
| Software Wiping | Moderate | Reusing or reselling functional hard drives (HDDs only). | Ineffective on damaged drives and modern SSDs; can be very slow. |
| Degaussing | High | Rapidly destroying data on large batches of magnetic media (HDDs). | Has zero effect on SSDs; leaves no visible proof of destruction. |
| Physical Shredding | Absolute | All drive types (HDD, SSD, tape) and for meeting strict compliance like HIPAA. | The drive is completely destroyed and cannot be reused. |
This table gives you a bird's-eye view, but let's dive into what each of these really means in practice.
Method 1: Software Wiping
Software wiping, or data sanitization, is the most basic approach. Think of your hard drive as a whiteboard covered in confidential meeting notes. Deleting a file is like erasing one word—the information is still there, just hidden from plain sight. Formatting the drive is like wiping the whole board, but a forensic expert could still recover faint impressions of what was written.
A proper software wipe is more aggressive, overwriting the drive multiple times with random data, often following protocols like the DoD 5220.22-M standard.
- The upside? This is the only method that leaves the hard drive functional, allowing for potential reuse or resale to recoup asset value.
- The downside? It’s an impractically slow process for large volumes of drives. Critically, it’s not reliable for damaged drives and is ineffective on modern Solid-State Drives (SSDs) due to their fundamentally different storage architecture.
Method 2: Degaussing
Degaussing is a specialized process exclusively for traditional Hard Disk Drives (HDDs). An HDD stores data on spinning magnetic platters. Degaussing uses a machine that generates an incredibly powerful magnetic field to instantly and permanently scramble the magnetic domains on those platters, turning organized data into an unreadable, chaotic mess. The drive is rendered completely inoperable.
- The upside? It’s extremely fast and effective for destroying data on large quantities of magnetic media.
- The downside? It only works on HDDs and magnetic tapes. It has zero effect on SSDs, which use non-magnetic flash memory. Another significant issue is that it leaves no visible proof of destruction, which can be a red flag for compliance auditors.
Method 3: Physical Destruction or Shredding
When there can be no margin for error, physical destruction is the definitive solution. This is the only truly foolproof method of hard drive destruction. An industrial shredder uses powerful steel teeth to grind the entire device—platters, chips, and casing—into tiny, confetti-like fragments, leaving absolutely no chance for data recovery.
The drive is fed into an industrial shredder that uses powerful steel teeth to grind the entire device—platters, chips, casing, and all—into tiny, confetti-like fragments.
This is the universal solution. It is equally effective on all media types: HDDs, SSDs, mobile phones, backup tapes, and more.
Because it physically annihilates the storage medium, shredding is the only method that guarantees 100% data elimination for all drive types. For any business handling sensitive PII, PHI, or financial data, or needing to meet strict compliance standards like HIPAA or FACTA, physical destruction isn't just an option; it's the gold standard.
If you want to go deeper, check out our complete guide on how to delete hard drive data securely. But the bottom line is this: physical shredding removes all doubt and delivers absolute peace of mind.
Meeting Data Destruction Compliance Standards
For any modern business, compliance isn't just a box to check—it's a legal shield protecting you from crippling fines and a damaged reputation. When it’s time to retire old hard drives, ignoring the rules can have devastating consequences. While navigating this web of regulations might seem intimidating, the core principle is actually pretty simple.
These rules exist to protect sensitive information. Whether it’s your customer's financial data, a patient's health records, or your own company's trade secrets, the law demands that this data be rendered permanently unrecoverable when the hardware is retired. This is where professional hard drive destruction becomes a non-negotiable part of your data governance strategy.
Translating Key Regulations into Action
Several major regulations dictate exactly how businesses must handle data at the end of its life. While each one has a slightly different focus, they all point to the same outcome: ensuring data is private and secure, right up to the moment it's physically destroyed.
Here are the key regulations your business needs to know:
- HIPAA (Health Insurance Portability and Accountability Act): The gold standard for patient privacy, HIPAA mandates that all Protected Health Information (PHI) must be rendered unreadable and non-recoverable before the media is disposed of. For healthcare organizations, understanding these strict rules is critical, as guides on secure data handling for healthcare providers make clear.
- FACTA (Fair and Accurate Credit Transactions Act): Focused on protecting consumers from identity theft, FACTA requires any business handling consumer credit information to take "reasonable measures" to destroy it—and it specifically cites physical destruction as a compliant method.
- NIST SP 800-88 (National Institute of Standards and Technology Special Publication 800-88): While technically a set of guidelines, NIST 800-88 has become the de facto standard for data sanitization across federal agencies and the private sector. It clearly defines methods for clearing, purging, and destroying data, with physical destruction being the ultimate solution for media that cannot be securely wiped.
The common thread is undeniable: your business must be able to prove the data is gone forever. This is exactly why simply deleting files or reformatting drives isn't just inadequate—it's dangerously non-compliant.
The Business Case for Compliance
Following these standards isn't just about avoiding penalties; it's about building customer trust and managing enterprise risk. As more businesses recognize the stakes, the demand for secure, certified disposal has grown significantly. The global hard drive destruction service market was valued at USD 1.5 billion in 2023 and is projected to reach USD 3.6 billion by 2032. This growth shows that proper data destruction is now viewed as a fundamental security control.
Compliance is your legal and ethical obligation to protect the people whose data you hold. When a hard drive leaves your possession, you are still responsible for what was on it—unless you can prove it was irretrievably destroyed.
This is why documentation is paramount. A professional destruction vendor provides a formal document that serves as your official record of compliance. You can learn more about how a Certificate of Destruction acts as your legal proof. This certificate confirms your media was destroyed according to all relevant laws, closing the loop on your data security duties and protecting your organization if an auditor ever comes knocking.
Choosing Between On-Site and Off-Site Destruction
Once your organization has committed to physical destruction, the next operational decision is where it will happen. Should a specialized shredding truck come to your facility, or is it more efficient to have your media transported to a secure plant? This choice between on-site and off-site hard drive destruction comes down to your company's specific requirements for security, cost, and compliance.
The entire decision centers on one critical concept: the chain of custody. This is the documented, unbroken paper trail that follows your sensitive IT assets from the moment they leave your control to the second they are destroyed. Any gap in that chain represents a potential security vulnerability.
On-Site Destruction: Maximum Security and Visibility
On-site destruction, or mobile shredding, brings the entire operation to your location. A self-contained, industrial-grade shredding truck arrives at your facility, and your hard drives are destroyed immediately, often while your staff watches. This method delivers the absolute highest level of security and transparency.
The key benefit is direct visual confirmation of destruction. There is no ambiguity and no period where your assets are in transit and out of your sight.
For organizations that handle incredibly sensitive data—like healthcare providers bound by HIPAA or government contractors with classified information—on-site destruction is often a non-negotiable requirement. It completely eliminates any risk of data getting lost or stolen in transit.
This approach provides a rock-solid, unbroken chain of custody that is easy to verify, offering total peace of mind and an ironclad record for compliance audits. If your business requires this ultimate level of assurance, exploring options for on-site shredding near you is the logical next step.
Off-Site Destruction: Efficiency and Cost-Effectiveness
Off-site, or plant-based, destruction involves a certified vendor collecting your hard drives in a secure, GPS-tracked vehicle and transporting them to a specialized facility for shredding. While you don't witness the destruction in person, a reputable partner maintains a strict and documented chain of custody from start to finish.
This is a highly secure and often more budget-friendly option, particularly for large-volume projects. A professional off-site process includes:
- Secure Collection: Trained, background-checked technicians arrive at your facility to pack all media into locked, tamper-proof containers.
- Documented Transport: Each container is scanned and logged before being moved to a secure, GPS-tracked vehicle for direct transport.
- Facility Destruction: At the secure plant, the drives are shredded under constant video surveillance, with the entire process documented.
- Certification: Following destruction, you receive a Certificate of Destruction detailing every serialized asset, providing a complete audit trail.
For many businesses, the cost savings and logistical simplicity of off-site services make it the ideal fit, provided you partner with a trusted, certified vendor who can validate their security procedures.
Making the Right Choice for Your Business
So, which service is right for your organization? The optimal choice depends on a careful assessment of your business needs. Consider these key factors:
- Data Sensitivity: Is your data governed by strict regulations like HIPAA or FACTA? If an in-transit data leak would be catastrophic, on-site is the safer choice.
- Internal Policies: Does your corporate security policy mandate that sensitive assets cannot leave the premises before being destroyed?
- Budgetary Constraints: Off-site destruction is generally more economical, enabling you to securely dispose of more equipment within your budget.
- Volume of Drives: For large-scale IT asset disposition projects, the logistics and cost of an off-site service are often far more practical.
Ultimately, both options provide exceptional security when performed by a certified, professional vendor. The decision hinges on your company's risk tolerance, compliance mandates, and operational priorities.
Why Proof of Destruction Is Your Legal Shield
Physically destroying a hard drive is a crucial security step, but from a business perspective, it’s only half the job. The real protection—the kind that stands up in an audit or legal dispute—comes from the official documentation proving you followed compliant procedures. Without this clear paper trail, you are leaving your organization exposed to significant liability.
This proof is delivered in two key documents: the Chain of Custody and the Certificate of Destruction. Understanding their function is what elevates a simple disposal task into a powerful risk management strategy.
Tracking Every Step with a Chain of Custody
Imagine shipping a high-value asset. You would demand a detailed log of every individual who handles it, from the moment it leaves your possession to its final destination. A Chain of Custody document provides exactly that for your sensitive IT assets.
It is a formal log that meticulously documents the secure transfer of your hard drives, capturing every critical detail to ensure there are no gaps where a drive could go missing.
A robust Chain of Custody record must include:
- Pickup Details: The exact date, time, and address of asset collection.
- Personnel Identification: The names and signatures of your designated employee and the vendor’s technician.
- Asset Inventory: A serialized list that uniquely identifies every single hard drive being transferred.
- Secure Transport: Confirmation that the media was secured in locked containers and transported in a GPS-tracked vehicle.
This document creates an unbroken, auditable trail from your facility to the point of destruction. It is your proof that you maintained control over your sensitive data until its secure transfer to a certified professional.
The Certificate of Destruction: Your Official Record
Once the shredding is complete, your vendor must issue a Certificate of Destruction. This is the official "death certificate" for your old hard drives. It is a legally binding document that serves as your final, definitive proof that the media was destroyed in full compliance with all applicable data protection laws.
This certificate is more than a receipt—it’s a detailed legal statement that closes the loop on your data security responsibilities. It is, without question, the single most important document you will receive in this process.
A Certificate of Destruction is not a "nice-to-have" option—it is a non-negotiable requirement. This document formally transfers liability from your organization to the destruction vendor and serves as your primary defense in a compliance audit.
For a certificate to be valid, it must include specific information: a clear reference to the Chain of Custody, the date and location of destruction, the exact method used (e.g., shredding to a specific particle size), and a list of the serialized assets that were destroyed. Without this, you have no verifiable proof, and your business remains vulnerable.
How to Select the Right Destruction Vendor
Choosing a partner for your company's hard drive destruction is far more than a simple procurement decision—it's a critical security appointment. You are entrusting a vendor with assets containing your most sensitive corporate information, from customer data and financial records to intellectual property. The right partner acts as an extension of your security program; the wrong one introduces catastrophic risk.
Before engaging with any vendor, the first step is an internal inventory assessment. You need a clear understanding of the number and types of drives (HDD vs. SSD) and their locations. This initial analysis will help you define the scope of the project and evaluate potential vendors more effectively.
Vetting Potential Vendors
Once you have inventoried your assets, the vetting process can begin. It is essential to look beyond marketing claims and scrutinize a vendor's security protocols, operational procedures, and professional credentials. While price is a factor, security and compliance must be the top priorities.
A vendor's certifications are the best indicator of their reliability and commitment to security. The most important credential to look for is NAID AAA Certification.
NAID AAA Certification is the gold standard in the data destruction industry. It’s a voluntary program that requires vendors to pass rigorous, unannounced audits covering everything from employee screening and training to operational security and the chain-of-custody process. A vendor with this certification has proven they are serious about protecting your data.
This certification is independent, third-party verification that a vendor's processes are secure, their employees are trustworthy, and their facility is protected. Choosing among qualified electronic waste disposal companies that hold certifications like NAID AAA is a fundamental step in mitigating risk.
Critical Questions to Ask Every Vendor
To make an informed decision, you must ask targeted questions that get to the core of a vendor's operations. Use this checklist to guide your vetting process:
-
Certifications and Compliance:
- Are you NAID AAA Certified? Can you provide a copy of your current certificate?
- How do you ensure compliance with regulations like HIPAA, FACTA, and NIST 800-88?
-
Employee Security Protocols:
- What kind of background checks do your employees undergo, and how often are they repeated?
- Are all employees who handle our media subject to drug screening and ongoing security training?
-
Process and Equipment:
- Can you describe your chain-of-custody process from the moment you pick up to the final destruction?
- What type of shredding equipment do you use? Is it capable of destroying both HDDs and SSDs to the required particle size?
-
Insurance and Liability:
- What are your liability insurance limits? Can you provide a certificate of insurance?
- Do you carry downstream data breach insurance?
The market for professional hard disk destruction equipment is expanding rapidly, reflecting a growing corporate commitment to data security. Valued at USD 2.69 billion in 2024, the market is projected to reach USD 4.23 billion by 2032. This growth is driven by commercial businesses investing heavily in certified solutions to meet strict compliance demands.
A professional, qualified vendor will welcome these questions and provide clear, confident answers. Their responses will give you a complete picture of their security posture, helping you select a partner you can trust to protect your business.
Common Questions About Hard Drive Destruction
When preparing for an IT asset disposition project, several key questions consistently arise. Getting clear, practical answers is crucial for making a secure and compliant decision that protects your organization. Here are some of the most common inquiries from businesses.
Are SSDs Destroyed Differently Than Hard Drives?
Absolutely, and this is a critical distinction for modern IT environments. Traditional hard disk drives (HDDs) store data on magnetic platters, which can be wiped by a powerful magnetic process called degaussing.
Solid-state drives (SSDs), however, use non-magnetic flash memory chips. Degaussing has zero effect on an SSD. For SSDs, the only method that guarantees complete data elimination is physical destruction. A specialized industrial shredder is required to pulverize the drive and its memory chips into unrecoverable fragments. You must confirm that your vendor's equipment is specifically rated to destroy SSDs.
What Happens to the Shredded Material?
After your drives are shredded into fragments, they are not sent to a landfill. The destroyed material, a mix of aluminum, plastic, and shredded circuit boards, is securely transported to a certified e-waste recycling facility.
There, the materials are sorted and processed. Metals are melted down for reuse in new products, and other components are repurposed. This responsible downstream process ensures your organization meets both its data security mandates and its environmental, social, and governance (ESG) goals.
Is Drilling Holes in a Drive Good Enough?
Drilling a hole through a hard drive is an inadequate DIY method that provides a false sense of security. Data on an HDD platter is stored across its entire surface; a drill bit only damages a small fraction of that area.
A determined actor with forensic tools could still potentially recover a significant amount of data from the platter's undamaged sections. For guaranteed, compliant security, professional shredding that destroys 100% of the drive's surface area is the only acceptable method.
How Do I Know a Vendor's Employees Are Trustworthy?
A reputable vendor will not ask for your trust; they will earn it with rigorous, third-party-audited certifications. The gold standard to demand is NAID AAA Certification, which holds data destruction companies to the strictest security standards.
This certification requires the vendor to conduct recurring criminal background checks, perform regular drug screening, and provide continuous security training for every employee with access to your assets. Before engaging any partner, demand proof of their NAID certification and review their employee screening policies. It is the only way to ensure your sensitive data is in safe hands.
Ready to ensure your company's data is destroyed securely and responsibly? The experts at Atlanta Computer Recycling provide certified hard drive destruction services that protect your business and guarantee compliance. Contact us today for a free consultation.