Eco-Friendly Computer Recycling: A Guide for Atlanta Businesses

For business leaders in Atlanta, that closet full of retired IT equipment is more than just clutter—it's a ticking time bomb of liability. Real eco-friendly computer recycling isn't just about being green. It's a core business strategy that shields your company from staggering financial, legal, and reputational damage.
Why Smart Recycling Is a Strategic Business Decision
Think of your old servers, desktops, and laptops like decommissioned bank vaults. Even when they're empty, you wouldn't just abandon them on a street corner, right? The same exact logic applies to your IT assets, which hold something far more valuable than cash: your company and customer data.
Tossing this equipment out with the regular trash is an open invitation for disaster. A single hard drive pulled from a landfill can trigger a catastrophic data breach, exposing sensitive files and shattering the trust you've built with your customers. The consequences aren't just theoretical—they come with very real costs that can haunt your bottom line for years.
The High Stakes of Improper Disposal
Failing to manage your retired IT assets properly exposes your business to a whole menu of preventable threats. Every outdated device is a potential weak spot if it's not handled by certified professionals. The risks hit you from all sides, affecting everything from your budget to your brand's integrity.
These risks include:
- Costly Data Breaches: One discarded hard drive with customer or employee data can spark a security firestorm, costing millions in remediation, notification services, and credit monitoring fees.
- Regulatory Fines: Getting on the wrong side of data protection laws like HIPAA for healthcare or Gramm-Leach-Bliley for finance can lead to crippling penalties. Regulators demand proof that you've securely destroyed the data.
- Lasting Brand Damage: News of a data breach travels fast. It erodes customer confidence and can permanently tarnish your company's reputation, sending clients running to competitors who take security seriously.
- Environmental Liability: Illegally dumping e-waste can result in hefty fines. Electronics are packed with toxic materials like lead and mercury that are heavily regulated by law.
Handling end-of-life IT assets is a crucial part of modern risk management. A responsible ITAD (IT Asset Disposition) program isn't an expense—it's an investment in your company's security, compliance, and reputation.
From Liability to Strategic Advantage
When you start looking at eco-friendly computer recycling as a strategic move, it stops being a chore and becomes a powerful defense. Partnering with a certified recycling expert ensures every single device is processed with airtight security. This goes way beyond just recycling the metal and plastic; it means you get a guaranteed, auditable process for destroying every last bit of stored data.
This approach completely neutralizes the risks tied to old hardware. Instead of being a source of liability, your retired assets become tangible proof of your company's commitment to security and responsibility. You can learn more about how a structured approach to corporate e-waste recycling protects your business. Making this strategic choice builds trust with clients, keeps regulators happy, and strengthens your brand as a responsible corporate citizen.
Understanding What 'Eco-Friendly' Really Means for E-Waste
The term "eco-friendly" gets thrown around a lot, but when we’re talking about retired IT assets, it means something very specific. It’s the difference between genuine corporate responsibility and accidentally fueling a global environmental crisis.
True eco-friendly computer recycling is about a secure, transparent, and certified process. It’s a guarantee that your old electronics won’t end up in a landfill or get illegally shipped overseas. The stakes are high—every server, laptop, and monitor contains a mix of both valuable resources and hazardous materials that demand expert handling.
When a circuit board from one of your old office computers gets tossed into a landfill, it doesn't just sit there. Toxic heavy metals like lead, mercury, and cadmium can eventually leach into the soil and groundwater, causing long-term damage. This is why partnering with a certified recycler is the only way to ensure a defensible and ethical chain of custody.
The Problem With Improper E-Waste Disposal
Uncertified recycling operations often take shortcuts, creating massive risks for your business and the planet. Instead of meticulously dismantling devices to recover materials, they might just load containers of e-waste and ship them to developing nations where environmental laws are weak or nonexistent.
This unethical practice creates two huge problems:
- Environmental Damage: In these places, workers often use crude methods like open-air burning to get to the precious metals inside, releasing toxic fumes and polluting local communities.
- Brand and Legal Risk: If your company’s branded assets are traced back to one of these dumpsites, the reputational damage can be devastating, not to mention the potential legal penalties.
The global e-waste crisis has hit staggering levels. The world generated 62 billion kilograms of electronic waste in 2022—an 82% increase from 2010. Shockingly, only 22.3% of it was properly collected and recycled, leaving an estimated $62 billion in recoverable natural resources completely lost.
This massive gap shows exactly why professional, certified recycling is so critical. It’s not just about getting rid of old gear; it’s about responsible resource management.
Embracing the Circular Economy
This is where the circular economy comes in. Instead of the old "take, make, dispose" model, the circular economy is all about keeping resources in use for as long as possible. Your old IT assets aren't just waste; they are a rich source of valuable materials waiting to be recovered.
Think of it as a high-tech urban mining operation. A certified recycler carefully de-manufactures each device to reclaim materials that can be fed right back into the manufacturing supply chain.
- Precious Metals: Gold, silver, copper, and palladium are extracted from circuit boards.
- Base Metals: Steel and aluminum from computer casings are separated and smelted for reuse.
- Plastics: Various types of plastics are shredded and sorted to become new products.
By transforming your retired assets back into raw materials, this process cuts down on the need for destructive mining and conserves huge amounts of energy. This is what it means to be truly "eco-friendly"—turning a potential liability into a valuable resource while protecting your company and the planet. To dig deeper, you can explore our article on the environmental impact of electronic waste and see how responsible recycling makes a tangible difference.
Securing Your Data Through Compliant IT Disposition
While the “eco-friendly” part of eco-friendly computer recycling is a huge win, for any business, the conversation has to start with data security. Before a single component gets recycled, every last bit of sensitive information on your retired assets must be permanently—and verifiably—destroyed.
A slip-up here isn’t just an operational mistake; it’s a direct threat to your company’s bottom line, legal standing, and public trust. When you hand over a server or a pallet of old laptops, you’re not just getting rid of hardware. You're entrusting a partner with the keys to your digital kingdom.
That’s why certified, compliant IT disposition isn't an optional add-on. It's the bedrock of any responsible asset retirement strategy. Anything less is just asking for trouble.
The goal is to make data recovery completely impossible, no matter what tools or techniques a bad actor might throw at it. Simply deleting files or reformatting a drive won't cut it—that's like tearing the table of contents out of a book and hoping no one can read the pages. The data is often still there, just waiting to be found.
The Gold Standard of Data Wiping
To get to true, irreversible data sanitization, the industry relies on proven, military-grade methods. The most recognized of these is the DoD 5220.22-M 3-pass wipe, a process that methodically overwrites your data with patterns of ones, zeros, and random characters.
Think of it like getting rid of a top-secret document:
- First Pass: You run the document through a shredder. This is the first overwrite, scrambling the original data.
- Second Pass: You take those shreds and douse them in black ink, making the original text impossible to read.
- Third Pass: Finally, you cover those inked-over shreds with random scribbles. The final pass ensures not even a trace of the original can ever be pieced back together.
This multi-pass approach ensures the original data is so deeply buried that it can never be reconstructed. It provides a defensible, auditable method for sanitizing hard drives and other storage media, which is non-negotiable for meeting compliance standards.
When Wiping Isn't Enough: Physical Destruction
Sometimes, a hard drive is too old, physically damaged, or just not worth the time to wipe reliably with software. In other cases, a company’s internal security policy might demand the most extreme level of security for devices that held top-tier intellectual property or customer data.
For these situations, there’s only one answer: physical destruction.
Hard drive shredding is the ultimate failsafe. This industrial process uses powerful machinery to literally grind drives into small, unrecognizable pieces of metal and plastic. There’s no software, no recovery tool, and no forensic lab on earth that can reassemble data from a pile of shredded bits. It provides absolute, undeniable certainty that the data is gone for good.
For organizations in highly regulated fields like healthcare or finance, having a documented and certified data destruction process isn't just a best practice—it's the law. A clear chain of custody, from the moment we pick it up to the moment it's destroyed, is your primary defense in an audit or security investigation.
Choosing the right method comes down to balancing security needs, compliance mandates, and the type of assets you're retiring.
To help Atlanta businesses make the right call, here’s a quick comparison of the primary data destruction methods.
Comparing Data Destruction Methods for Business Assets
| Method | Process Description | Security Level | Best For | Compliance Alignment |
|---|---|---|---|---|
| Data Wiping (DoD 5220.22-M) | Software overwrites drive sectors multiple times with random data patterns. | High | Reusable assets, devices intended for remarketing, standard corporate data. | Meets most NIST 800-88, HIPAA, and GLBA requirements for data sanitization. |
| Degaussing | Uses a powerful magnetic field to instantly erase all data from magnetic media like HDDs and tapes. | Very High | End-of-life magnetic storage; renders the drive inoperable. | Aligns with high-security government and defense standards. Not effective for SSDs. |
| Physical Shredding | Industrial machinery grinds the entire storage device into small, irrecoverable fragments. | Absolute | Damaged drives, SSDs, devices with top-secret data, or when policy mandates total destruction. | Exceeds all major compliance standards (HIPAA, SOX, GLBA) by ensuring data cannot be recovered. |
Ultimately, the best strategy often involves a combination of these methods, tailored to the specific devices and data sensitivity levels within your organization.
Connecting Data Destruction to Compliance
This level of detail is especially critical for any business operating under strict regulatory frameworks. Failing to prove you securely destroyed sensitive data can lead to staggering fines, legal battles, and a damaged reputation that’s hard to rebuild.
- Healthcare (HIPAA): The Health Insurance Portability and Accountability Act demands that all patient health information (PHI) be rendered completely unusable and unreadable before an electronic device is disposed of.
- Finance (GLBA/SOX): The Gramm-Leach-Bliley Act and Sarbanes-Oxley Act require financial institutions to protect consumer financial data with ironclad security protocols, including during asset retirement.
- General Data Privacy (GDPR/CCPA): Even if you aren't in a specific industry, broad data privacy laws like GDPR and CCPA mandate the secure handling and disposal of all personal information.
Working with a certified ITAD partner ensures these complex rules are followed to the letter. You’ll receive a formal Certificate of Data Destruction, an official document that serves as your proof of compliance. This certificate lists the serial numbers of the devices processed and confirms the destruction method used, giving you the clean, auditable trail needed to satisfy regulators and protect your business.
For a deeper dive into the available methods, our overview of secure data destruction services offers additional insights.
Building Your Corporate IT Asset Disposition Policy
A truly effective eco-friendly computer recycling program doesn’t just happen. It’s built on a clear, well-defined corporate policy. This is where you move from good intentions to a formal IT Asset Disposition (ITAD) policy—a blueprint that guides every single step of a device's retirement. This document turns your goals into a process that’s repeatable, defensible, and efficient.
Without a formal policy, retiring old equipment can get chaotic fast. Decisions are made on the fly, security measures are all over the place, and your company is exposed to the very risks you were trying to avoid. A solid ITAD policy takes the guesswork out of the equation, making sure everyone knows exactly what to do when a computer, server, or phone hits its end-of-life.
Before you dive in, it’s crucial to understand the difference between policy and procedure. Your policy sets the "why"—the high-level rules and goals. The procedures will come later, defining the "how" with step-by-step instructions.
Core Components of an Effective ITAD Policy
Think of your ITAD policy as the official rulebook for handling old tech. It needs to be a comprehensive guide that covers everything from the moment a device is flagged for retirement to its final, documented disposal. It must be clear, actionable, and perfectly aligned with your business’s security, financial, and environmental goals.
Here’s what every strong policy should include:
- Asset Retirement Triggers: Define precisely what kicks off the retirement process. Is it age? Maybe all laptops over four years get replaced. Is it performance? Or the end of a warranty or lease? Spell it out.
- Data Security Protocols: Get specific about data destruction. Your policy must mandate certain methods for different types of data. For instance, you might require that all hard drives with sensitive customer data undergo physical shredding, while others can be securely wiped using the DoD 5220.22-M standard.
- Environmental Standards: Put your commitment to responsible recycling in writing. This section should require that all e-waste is handled by certified partners who follow a zero-landfill policy and can prove they don’t export hazardous materials.
- Chain of Custody Requirements: Outline the paper trail you need. This means detailing every piece of documentation, from asset inventory lists and secure transport logs to the final Certificate of Data Destruction. This creates an unbroken, auditable record for total compliance.
Deciding Between Remarketing and Recycling
One of the most important strategic decisions your policy will address is what to do with retired assets. Should they be refurbished and sold, or should they be securely recycled? The right answer depends on the gear’s age, condition, and current market value. Your policy needs to provide clear guidelines to make this call consistently.
The primary goal is to maximize value recovery without compromising data security or environmental principles. A well-structured policy empowers your team to make smart, consistent decisions that benefit the bottom line and uphold corporate responsibility.
This isn't an all-or-nothing game. A smart, flexible policy creates a hybrid approach:
- Asset Remarketing: For newer, functional equipment like recent-model laptops or in-demand servers, refurbishment and resale can bring back a significant return. The policy should specify which assets are eligible and absolutely require that all data is wiped to certified standards before any resale happens.
- Secure Recycling: For anything that's too old, broken, or proprietary to have resale value, the policy should mandate immediate, secure recycling. Here, the focus shifts entirely to guaranteed data destruction and environmentally sound material recovery.
By defining these two clear paths, your ITAD policy creates a system that pulls value from assets when possible and guarantees security and compliance for everything else. It transforms asset retirement from a logistical headache into a strategic part of your IT management lifecycle.
The Logistics of Secure E-Waste Pickup and Processing
Once your ITAD policy is in place, it’s time to put it into action. This is where partnering with a professional e-waste recycler takes all the guesswork out of the equation. We turn what could be a massive logistical headache into a simple, secure, and streamlined operation. The process doesn’t start when a truck shows up—it begins with a clear plan built around your business needs, ensuring zero disruption from start to finish.
It all kicks off with an initial consultation. You tell us what you have, whether it’s a few dozen laptops from an office refresh or multiple server racks from a full data center decommissioning. Based on that inventory, we’ll schedule a pickup that works around your business hours, so your team can keep doing what they do best without interruption.
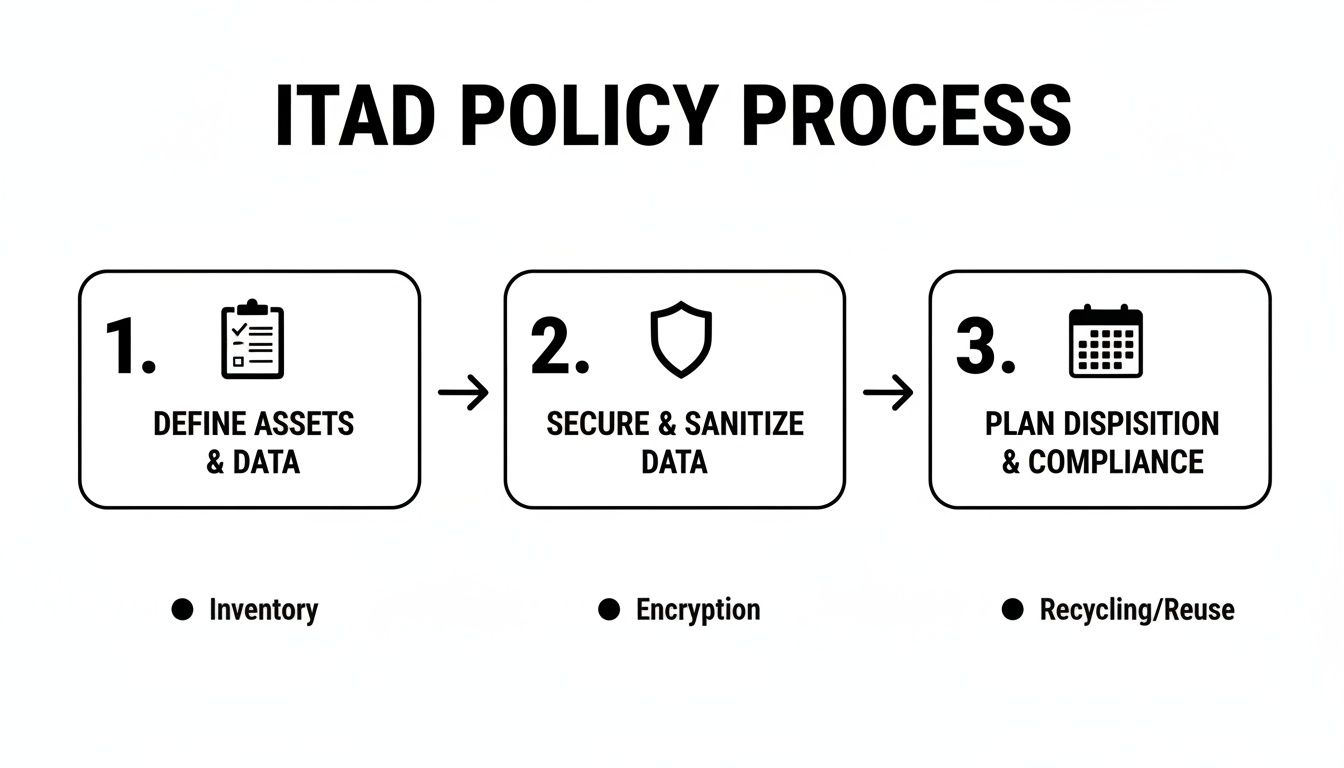
This flowchart lays out the core steps of a solid ITAD process.
As you can see, a successful program starts with defining your assets, locking down the data, and then mapping out the disposal logistics.
On-Site Execution with Precision and Security
On pickup day, our professional team arrives ready to handle every detail. This isn’t a simple curbside pickup; it's a white-glove logistical service designed for a commercial environment. Our crew is trained to work quietly and securely, even in an active office.
- For office environments: Our technicians can move from floor to floor, gathering desktops, monitors, and other peripherals right from workstations or storage closets. Everything is carefully packed into secure, sealed containers before it leaves your sight.
- For data centers: Our team can perform on-site de-installation, carefully removing servers and networking equipment from racks before they are loaded for transport.
Every single item is meticulously inventoried before it leaves your facility. This creates the first, crucial link in an unbroken chain of custody, giving you a documented trail for compliance and complete transparency.
Peace of mind comes from knowing your assets are handled by a dedicated, professional team from the moment they leave your control. The equipment is transported in a secure, dedicated vehicle directly to the processing facility—never co-mingled with other materials or left unattended.
This disciplined approach is vital. The global electronic waste recycling market is projected to hit $80.4 billion USD in 2025. Yet, while the United States generates a staggering 6.92 million tonnes of e-waste each year, our recycling rate is stuck at a dismal 15%. This gap highlights the urgent need for certified, professional services to step in and do the job right.
Final Processing and Certified Documentation
Once your assets arrive at our secure facility, the final steps begin. Every data-bearing device undergoes the certified destruction method you specified in your policy, whether that’s DoD-compliant wiping or physical shredding. After the data is gone for good, the assets are sorted and dismantled for responsible materials recovery.
The entire process wraps up with the delivery of a Certificate of Destruction. This is your official record. It lists the serial numbers of every asset we processed and confirms that all data was verifiably destroyed, giving you definitive proof of compliance for any internal or external audits. It’s the final step that closes the loop on a secure, transparent, and professionally managed ITAD process.
To see how we manage everything from start to finish, learn more about our commercial computer pickup services in Atlanta.
Choosing the Right ITAD Partner in Atlanta
Picking the right IT Asset Disposition (ITAD) partner isn't just about getting rid of old equipment—it's a critical business decision. The company you choose has a direct impact on your data security, your compliance with regulations, and even your brand's reputation. A true partner isn't just a vendor; they become an extension of your IT and risk management teams.
The first thing to look for is a partner with a transparent and verifiable process. This means everything from certified data wiping using standards like DoD 5220.22-M to physical hard drive shredding for absolute certainty. They should be able to manage secure on-site logistics, handling the entire process from packing to transport with an unbroken chain of custody.
Key Differentiators for an Atlanta Partner
There are real advantages to working with a local Atlanta-based specialist, especially when you’re tackling a complex project like a bulk office cleanout or a full data center decommissioning. A local team knows the area, understands the logistics, and can respond much faster than a national provider trying to coordinate from afar.
Here are the non-negotiables to look for:
- Certified Data Destruction: You need undeniable proof that every bit of your data has been permanently erased.
- A Zero-Landfill Policy: This is a firm guarantee that 100% of your assets will be responsibly recycled or remarketed, never dumped.
- On-Site Capabilities: Your partner should have the ability to come to your facility to de-install servers, pack up assets, and manage the entire removal with minimal disruption to your team.
Running a thorough vendor risk assessment is an essential part of this process. You need to dig into their certifications, security protocols, and who their downstream recycling partners are to ensure they meet your company's high standards.
Beyond Disposal: A Strategic Partnership
The best ITAD partners help you view eco-friendly computer recycling as a core piece of your corporate strategy. They're your shield, protecting your brand from the fallout of a data breach or an environmental misstep. Globally, recycling standards vary dramatically. Europe, for example, has a formal collection and recycling rate of 42.8%, which is more than double the global average. That figure puts the Americas (30%) and Asia (just 11.8%) to shame, highlighting why it’s so important to work with a partner who holds themselves to the highest possible standard.
Your ITAD provider should be your frontline defense against data liability and your proof of commitment to corporate social responsibility. They provide the certified documentation needed to satisfy auditors and stakeholders alike.
By choosing a partner who provides complete, end-to-end management, you get both peace of mind and a verifiable record of responsible stewardship. Atlanta Computer Recycling is ready to be that partner, helping you turn retired IT assets from a potential liability into a documented strength. For more details on our approach, check out our guide on finding the right electronic waste recycling company.
When you’re ready, contact us for a straightforward quote and see how we can help.
Your Questions Answered: Business Computer Recycling FAQ
Even with a solid ITAD plan in place, we find that Atlanta business leaders usually have a few practical questions before getting started. It's smart to clarify the details. Getting straight answers is the best way to feel confident you're choosing the right partner.
Here are the most common things we get asked by our commercial clients.
Does Your Business Recycling Service Have a Cost?
For the vast majority of our commercial clients right here in the Atlanta metro area, our professional pickup and recycling services are provided at no charge. That standard, no-cost service even includes our DoD-compliant data wiping for every hard drive we collect, so your data security is covered without an extra fee.
The only time a cost might come into play is for highly specialized jobs. Think on-site hard drive shredding, a major equipment de-installation from a data center, or a pickup scheduled far outside our usual service radius. We believe in being upfront, which is why we always give you a detailed, no-obligation quote before any work begins. You'll know exactly what to expect.
What Types of Business Equipment Do You Accept?
We focus exclusively on commercial IT assets. That's our specialty. It allows us to be incredibly efficient and secure for the businesses, schools, and healthcare facilities we serve.
We’re set up to handle pretty much any IT gear you need to retire, including:
- Desktops, laptops, and workstations
- Servers and all types of data center equipment
- Networking gear like switches, routers, and firewalls
- Monitors (both LCD and LED)
- All the related peripherals—keyboards, mice, and mountains of cables
We're fully equipped for bulk disposals, whether you're clearing out an entire office, managing a company-wide tech refresh, or decommissioning a complex data center. Our commercial focus means we have the right team and the right tools for your specific job.
The most critical piece of documentation you will receive is the Certificate of Data Destruction. This official record is your proof of compliance for audits and internal governance, confirming that all data was eliminated according to industry-best practices.
How Do We Receive Proof That Our Data Was Destroyed?
Once your equipment is securely back at our facility and processed, we issue a formal Certificate of Data Destruction. This isn't just a receipt—it's a critical document for your company’s risk management and compliance records.
The certificate provides a clear, auditable trail, detailing the items we processed and confirming the exact method used to eliminate the data. For your organization, it's the official proof that you've met your obligations under regulations like HIPAA, protecting you from the legal and financial fallout of a data breach.
Are Your Recycling Processes Environmentally Certified?
Absolutely. We take our environmental commitments just as seriously as our data security promises. That's why we only work with downstream partners who are R2 and e-Stewards certified. These are the gold standards in the electronics recycling industry, and we don't settle for anything less.
This partnership guarantees that every single component from your old IT gear is managed responsibly and ethically. It means 100% of your e-waste stays out of landfills, and no hazardous materials are shipped overseas. It’s about protecting the environment, but it’s also about protecting your company’s reputation as a good corporate citizen.
Ready to put a secure, compliant, and environmentally sound ITAD program in place for your Atlanta business? Contact Atlanta Computer Recycling today. We can schedule your no-cost pickup and help protect your company's data and its good name. Learn more at https://atlantacomputerrecycling.com.