How to Wipe a Hard Drive Securely: A Guide for Businesses

When it's time to retire old hardware, simply dragging files to the trash is a significant security risk. Properly wiping a hard drive means using specialized methods to completely overwrite the disk, making the original information unrecoverable. For businesses, this isn't just a technical task—it's a critical component of risk management.
Merely hitting 'delete' or formatting a drive is a common but dangerous mistake. These actions only remove the pointers to the data, leaving the actual files easily accessible with basic recovery tools and exposing your company to a potential data breach.
The Hidden Dangers of Improper Hard Drive Disposal
Many business leaders believe that a simple file deletion or a quick drive format is sufficient protection. This is a massive, and potentially very costly, misunderstanding of how data is stored and the liabilities involved.
When you "delete" a file, the operating system simply marks that space as available for new data. The original ones and zeros are still there, perfectly intact, waiting to be overwritten. It’s like removing a book's card from the library catalog but leaving the book itself on the shelf. Anyone with the right tools can still find it.
This vulnerability is easily exploited by off-the-shelf data recovery software, which can piece together "deleted" files. Suddenly, sensitive corporate financials, confidential client records, and your valuable intellectual property are exposed.
A Cautionary Tale of Data Negligence
This isn't a theoretical threat. Consider a company that sold an old server on an online marketplace, thinking a quick format was good enough. They ended up handing over thousands of confidential customer files without even knowing it. The resulting data breach cost them a seven-figure fine from regulators, not to mention the permanent damage to their reputation.
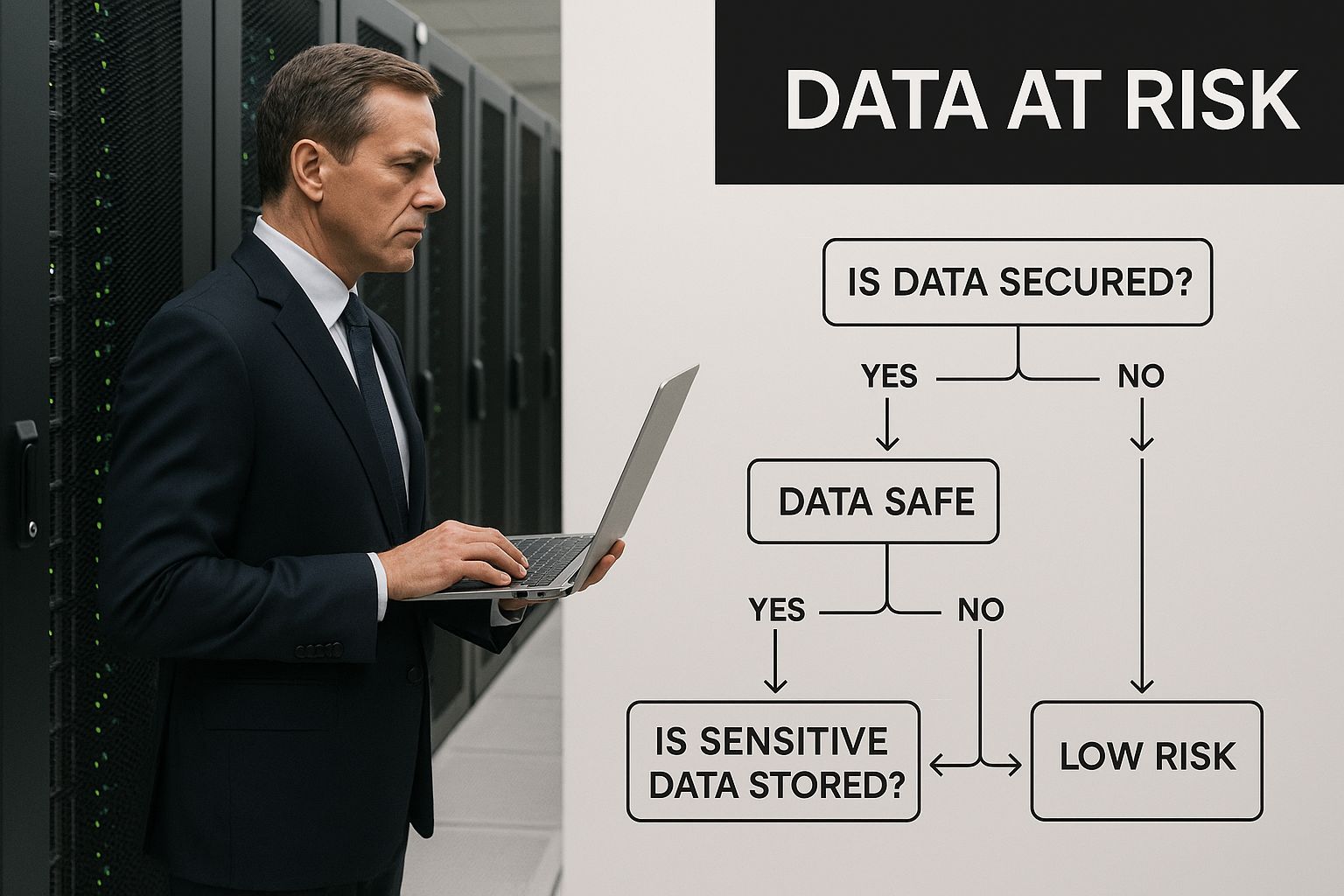
This infographic gives a clear picture of where data remains at risk throughout a device's lifecycle.
As the image shows, data security is a continuous process from device acquisition to final disposal. One weak link breaks the entire chain. Secure data destruction isn't just an IT chore; it's a core part of your company’s risk management and compliance strategy.
It's no surprise that the demand for professional data destruction is booming. The global market, currently valued at over USD 17 billion, is expected to skyrocket to nearly USD 52.96 billion by 2033. This explosive growth is driven by stricter compliance laws like GDPR and HIPAA and the increasing need for businesses to provide auditable proof of their due diligence.
Key Takeaway: Failing to properly wipe a hard drive is a direct threat to your company's financial stability, legal standing, and public trust. The potential costs of a data breach far outweigh the investment in professional, secure disposal services.
Ultimately, understanding these risks is the first step toward building a secure IT asset disposition (ITAD) plan. This also ties into the broader challenge of managing e-waste responsibly, which you can learn more about in our guide on the environmental impact of electronic waste.
Choosing The Right Data Destruction Method for Your Business
Figuring out the right way to wipe a hard drive isn't just a technical task—it's a critical business decision that directly impacts your security, compliance, and budget. The three primary methods are software wiping, degaussing, and physical destruction. Each has its place, and the choice depends on the hardware type and your asset recovery strategy.
Let's review these options to help you confidently decide when to securely reuse a drive and when you must destroy it to eliminate all risk.
Software-Based Wiping for Hardware Reuse
When your IT asset management plan includes reusing or reselling hardware, professional software wiping is the correct method. This process, also known as data erasure, uses specialized programs to systematically overwrite every bit of data on a drive. The original information becomes completely unrecoverable, but the drive itself is left perfectly functional for redeployment or resale.
Adhering to industry standards is non-negotiable for proving due diligence. The two most important standards for businesses are:
- DoD 5220.22-M: This classic 3-pass overwrite standard, once used by the U.S. Department of Defense, is a thorough and widely recognized method suitable for traditional magnetic hard drives (HDDs).
- NIST 800-88: The National Institute of Standards and Technology provides the modern gold standard. This up-to-date framework accounts for different hardware types, recommending specific commands like "Secure Erase" for HDDs and "Sanitize" for Solid-State Drives (SSDs).
A professional software wipe is the ideal choice for end-of-lease equipment returns, internal asset redeployment, or preparing devices for employee purchase programs. A firm grasp of these standards is fundamental to any strong corporate data security strategy.
Degaussing and Physical Destruction for End-of-Life Assets
Sometimes, a drive is too old, it has failed, or the data it contains is so sensitive that reuse is simply not an option. That’s when you need methods that render the hardware permanently useless.
Degaussing blasts traditional HDDs and magnetic tapes with an incredibly powerful magnetic field, scrambling the magnetic platters where data is stored. It’s extremely fast and highly effective for that specific type of media. However, degaussing is completely useless on modern SSDs, which rely on flash memory with no magnetic components.
Physical destruction is the final, irreversible solution. This means shredding, crushing, or pulverizing the drive into tiny, unsalvageable fragments. For businesses handling HIPAA-protected health information, financial data, or proprietary IP, shredding is often the only acceptable path. It offers absolute, verifiable proof that the data is gone forever.
When you're looking for a professional partner to handle this, companies like Techwaste Recycling LLC, offering data destruction services, are set up to provide the comprehensive e-waste recycling and certified data destruction that today's compliance landscape demands.
In the end, it all boils down to a risk assessment: can this drive be safely sanitized for a second life, or is the risk too great, demanding total destruction?
Comparing Data Destruction Methods for Business Assets
To make this decision easier, here’s a side-by-side look at the top three data destruction methods. This table breaks down which approach is best for your specific business needs and hardware.
| Method | Best For | Hardware Reusable? | Security Level | Compliance Notes |
|---|---|---|---|---|
| Software Wiping | Reusing or reselling modern HDDs and SSDs. | Yes | High (NIST 800-88 compliant) | Provides an auditable certificate of erasure. |
| Degaussing | Rapidly sanitizing magnetic tapes and old HDDs. | No | Very High (for magnetic media only) | Ineffective for SSDs; physical damage is visible. |
| Physical Shredding | End-of-life, damaged, or highly sensitive drives. | No | Absolute | Best for HIPAA/GDPR; provides a certificate of destruction. |
By aligning the right technique with your compliance requirements and asset management goals, you can build a data destruction process that is both secure and cost-effective for your business.
Using Professional Data Erasure Software
When your business needs to reuse or redeploy hardware, engaging a professional service that uses enterprise-grade data erasure software is the smartest move. This isn't about downloading a free tool and hoping for the best. It's about a documented, certified process that delivers undeniable, auditable proof that your data is gone for good.
Professional platforms are built for business workflows. Imagine needing to wipe 100 laptops from a sales team that just upgraded their gear. Professional software allows a certified vendor to manage the entire project from a central console, wiping every device simultaneously. That’s a level of efficiency and control you simply won't find with consumer-grade tools.
Mission-Critical Features for Business Compliance
For any business, especially in regulated industries like healthcare or finance, documentation is paramount. A successful data wipe means nothing if you can't prove it happened. That’s why the single most important feature of any professional data erasure process is its reporting capability.
After a successful wipe, the vendor must generate a detailed, tamper-proof certificate of erasure for each hard drive. This document is your proof of compliance during an audit, demonstrating you followed industry best practices.
When evaluating a data wiping service, ensure they explicitly support:
- International Standards: The process must adhere to protocols like NIST 800-88 and DoD 5220.22-M. This is non-negotiable.
- Scalable Deployment: The provider must be equipped to handle dozens or even hundreds of devices at once.
- Certified Audit Trails: You need tamper-proof logs and certificates that confirm every detail of the erasure process for your records.
This level of documentation isn't just a "nice-to-have"—it's your frontline defense against crippling fines and the reputational damage that follows a data breach.
Imagine breezing through your next HIPAA or GDPR audit. Instead of scrambling for proof, you simply present a folder of detailed erasure certificates that verify your company’s due diligence for every single retired asset.
The Growing Market for Secure Erasure
The demand for these robust solutions is surging as organizations worldwide face stricter data privacy laws. Just last year, the data wipe software market was valued at a staggering USD 2.2 billion in North America alone and is projected to more than double by 2033.
This growth is being driven by the need to comply with regulations like GDPR and CCPA and to protect against the constant threat of cyberattacks. As you learn more about the global demand for data wipe software, it becomes clear that investing in certified erasure is now a standard cost of doing business securely.
When Physical Destruction Is the Only Answer
While professional software can securely wipe a hard drive for reuse, some situations are too risky for anything less than total physical destruction. This is when shredding becomes the only responsible path forward. For many businesses, especially in regulated industries, it's not a choice—it's a mandatory step in their data disposal policy.
From a risk management perspective, attempting to wipe a physically damaged or failing hard drive is a gamble. The wiping process might fail, leaving recoverable fragments of sensitive data behind. In these scenarios, the only way to guarantee 100% data irretrievability is to destroy the drive itself.
Key Triggers for Physical Destruction
The decision to shred a drive is a strategic one based on clear risk factors. Your business should always opt for destruction in these common scenarios:
- Failed or Damaged Hardware: If a drive is physically broken, has bad sectors, or won't boot, a software wipe is unreliable. Shredding it is the only secure option.
- Containing Top-Secret Data: When dealing with invaluable intellectual property, trade secrets, or classified information, the potential resale value of a drive is dwarfed by the risk of exposure. Destruction eliminates all doubt.
- Regulatory Mandates: Industries like healthcare (HIPAA) and finance have strict end-of-life policies that often require physical destruction to ensure compliance and avoid crippling penalties.
Do-it-yourself methods like drilling holes or taking a hammer to a drive are a critical mistake. A determined data thief can still recover data from surviving platter fragments. Only industrial-grade shredding, which pulverizes a drive into tiny, unrecognizable pieces, meets the security standards your business requires.
Crucial Takeaway: For end-of-life, damaged, or highly sensitive drives, industrial shredding is the gold standard. It provides an absolute, verifiable end to the data lifecycle that no DIY method can match.
The Importance of Certified Destruction
There's a reason the professional hard drive shredding market is booming. It was valued at USD 0.72 billion recently and is on track to hit USD 1.2 billion by 2033. This isn't just a trend; it's a reflection of a growing corporate understanding that secure disposal is a non-negotiable business function. You can dive deeper into the research behind the hard drive shredding market to see for yourself.
When you partner with a certified vendor, the entire process is meticulously documented. They provide a Certificate of Destruction when the job is done—a legal document that serves as your official proof of compliance.
This certificate creates an unbroken, auditable chain of custody from the moment the drives leave your facility, protecting your business from future audits or legal challenges. This level of verification is essential when managing large-scale projects, such as professional data center equipment disposal.
So, you need to physically destroy hard drives. This is one of those critical decisions where the choice between on-site and off-site destruction has real consequences for your security, logistics, and budget.
Honestly, neither option is flat-out better than the other. The right call comes down to your company's risk tolerance and operational reality.
On-site destruction is exactly what it sounds like: the shredder comes straight to your doorstep. For many organizations, especially those in government, healthcare, or finance, this is the only way to go. There’s a huge sense of security in physically witnessing the destruction yourself. It provides an unbroken chain of custody, which is often a non-negotiable requirement for passing tough compliance audits.
This approach completely sidesteps the risks of transporting drives loaded with sensitive data. When the entire process happens under your roof, there's zero chance of a drive getting lost in transit.
The Case for Off-Site Destruction
On the other hand, off-site services are hard to beat for efficiency and cost, particularly for massive jobs like a data center decommissioning or an office-wide hardware refresh. A certified vendor takes care of everything—from secure collection and transport to the final destruction at their specialized facility. This frees up your team to do their actual jobs instead of babysitting a shredding truck for hours.
Off-site is also the most practical solution for businesses that just don't have the space for a giant shredding truck or want to keep workplace disruptions to an absolute minimum.
Key Insight: This decision isn't just about security; it's about workflow. On-site gives you maximum transparency for your most sensitive data. Off-site gives you maximum efficiency for large-volume disposals.
Non-Negotiable Security for Off-Site Services
If you do go the off-site route, you absolutely must verify the vendor's security protocols. You're handing over your most sensitive assets, so trust has to be backed by proof. A reputable partner will always deliver on the following:
- Secure Chain of Custody: The process must start with locked, tamper-evident bins to collect the drives at your location.
- GPS-Tracked Transport: Every vehicle moving your assets needs to have real-time GPS tracking. No exceptions.
- 24/7 Facility Monitoring: The destruction facility itself has to be under constant surveillance with tightly controlled access, protecting your assets from the moment they arrive.
When your IT assets are ready for disposal, you can feel confident in a secure process, whether you choose on-site or off-site services. To get started and see what works best for you, you can easily schedule a pickup for your business IT equipment and make sure your data is handled responsibly. It’s a simple step that aligns your company’s security needs with a clear, actionable plan.
Building Your Company's Data Disposal Policy
Knowing how to wipe a hard drive is one thing. Turning that knowledge into a consistent, defensible company strategy is another ballgame entirely. That’s where a formal data disposal policy comes in. This document isn't just bureaucratic red tape; it’s the blueprint that transforms scattered best practices into official company procedure.
Without one, data destruction often becomes a messy, ad-hoc process handled differently by each department—or worse, not at all. A strong policy is your first line of defense against both accidental data leaks and the massive fines that come with non-compliance. Regulations like GDPR, HIPAA, and CCPA don’t just ask if you destroyed data; they demand proof of how and when it was done, with clear, repeatable steps.
Core Components of a Defensible Policy
A truly effective policy is a living document that outlines your entire data end-of-life process. It needs to clearly define the who, what, when, and how of asset disposition for everyone in your organization.
To make sure your policy is audit-ready, it should include these key elements:
- Data Classification Tiers: Not all data is created equal. Define different levels of sensitivity—like Public, Internal, Confidential, and Restricted—to determine how each type must be handled. Public marketing materials don’t need the same rigorous destruction as protected health information (PHI).
- Assigned Destruction Methods: Link each data classification to a specific disposal technique. For example, you might state that drives with "Confidential" data require a NIST 800-88 compliant software wipe, while anything marked "Restricted" mandates on-site physical shredding. No ambiguity.
- Chain of Custody Protocol: Detail every single step, from the moment an asset is taken offline to its final destruction. This log should track who is authorized to handle the assets and what documentation is required at each stage.
- Documentation and Retention Rules: This is critical. Your policy must require a Certificate of Erasure or a Certificate of Destruction for every single asset. It should also state exactly how long these records must be kept to satisfy auditors.
When you're ready to formalize your company's approach, focus on creating a comprehensive data retention and disposal policy that leaves no room for error. A solid framework transforms a recurring IT headache into a secure, repeatable business process.
Partnering for Policy Implementation
Creating the policy is the first half of the battle. Actually implementing it consistently is what keeps you protected. This is where partnering with a certified IT asset disposition (ITAD) vendor becomes a smart move.
An expert partner handles the complex logistics and provides the certified documentation you need to prove your policy is being followed to the letter. This guidance is especially valuable when navigating the complexities of IT equipment disposal services for Atlanta businesses. A robust policy, backed by a professional partner, is the surest way to make your data disposal process secure, compliant, and rock-solid.
At Atlanta Computer Recycling, we help businesses implement and execute secure data disposal policies with certified wiping and shredding services. Ensure your company is protected by partnering with the experts. Learn more about our ITAD solutions.