How to Wipe a Hard Drive Completely: A Guide for Businesses

When decommissioning IT assets, many businesses make a critical error: assuming a standard format or deleting files is enough to protect sensitive corporate data. This common oversight doesn't just leave data accessible; it exposes your organization to significant financial, legal, and reputational risks.
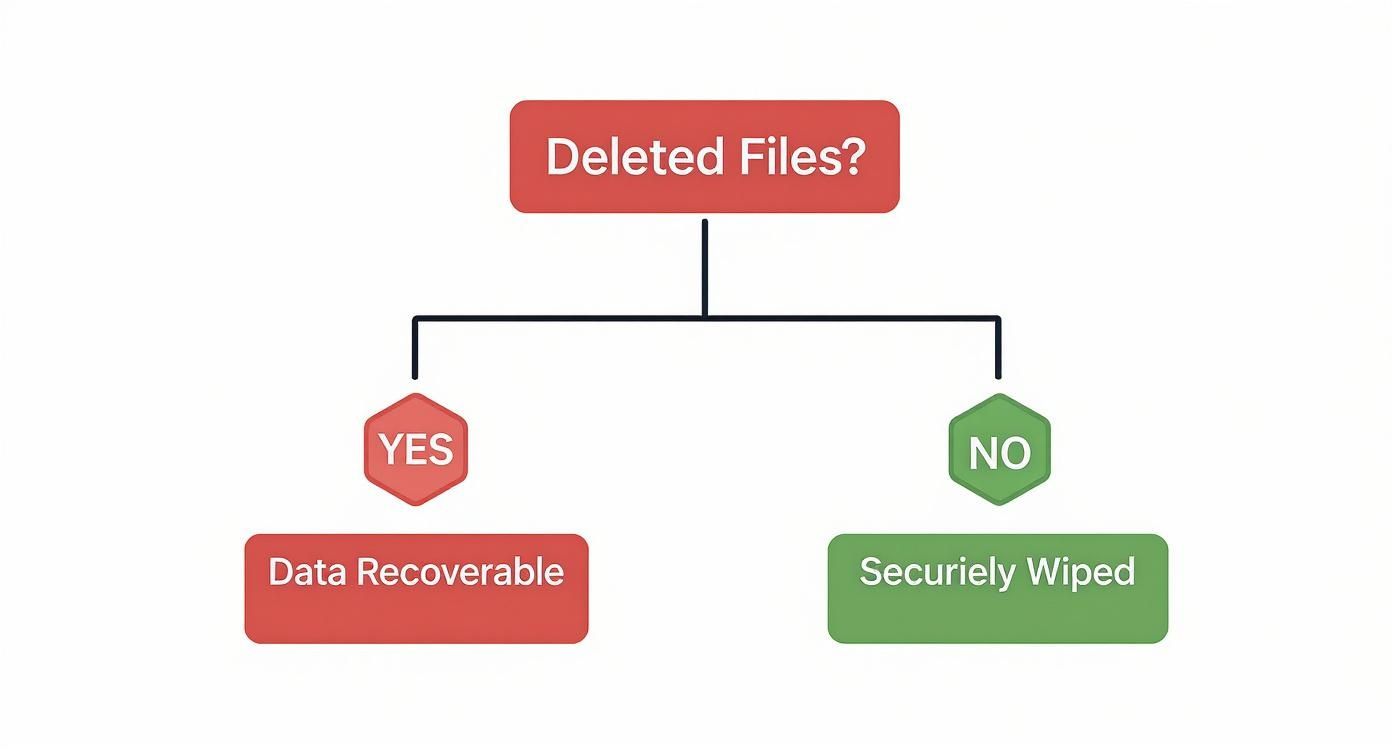
Simply deleting files does not erase them. The process is akin to removing the table of contents from a book—the pages containing your sensitive corporate data, customer details, and trade secrets remain intact, easily readable by anyone with basic data recovery software.
The Hidden Dangers of Improper Hard Drive Disposal
The consequences of improper data disposal are not hypothetical. Consider a mid-sized healthcare provider that decommissioned a server, performed a standard format, and sent it for recycling. Months later, the organization faced a catastrophic data breach after that exact drive was acquired on the secondary market. The result was the exposure of thousands of patient records, leading to crippling HIPAA fines and irreversible damage to their reputation.
This vulnerability stems from how operating systems handle file deletion. When a file is "deleted," the system merely marks the space it occupies as available for new data. The original information remains recoverable until it is overwritten.
This leaves a trove of sensitive data on any decommissioned business device:
- Customer Information: Full names, addresses, credit card numbers, and contact lists.
- Financial Records: Company budgets, payroll details, and confidential financial statements.
- Intellectual Property: Trade secrets, proprietary research, and internal strategy documents.
The risk is tangible and escalating, with frequent reports on incidents like the rising threat of infostealer malware and leaked personal data. These events underscore the critical importance of implementing a secure data destruction protocol.
To fully grasp the stakes, it is essential to understand the difference between standard deletion and secure, professional wiping.
Deletion vs. Secure Wiping: Understanding the Business Risk
| Method | What Actually Happens | Data Recoverability | Business Risk Level |
|---|---|---|---|
| Standard Deletion | The file's pointer is removed, but the data remains on the drive. | High. Easily restored with common, often free, software. | Extreme. Leaves the business open to data breaches, compliance fines, and reputational damage. |
| Secure Wiping | The drive is overwritten multiple times with random data, destroying the original information. | Extremely Low. Requires highly specialized, expensive forensic tools with no guarantee of success. | Minimal. The data is forensically unrecoverable, protecting the business from liability. |
This comparison makes it evident that relying on standard deletion is a gamble no responsible organization can afford to take.
Data Wiping is a Core Business Strategy, Not an IT Chore
Secure data wiping is not merely an IT task; it is a foundational component of a robust risk management strategy. It is essential for protecting your business from financial penalties, legal action, and the kind of reputational damage that can take years to repair.
The market reflects this growing imperative. The global secure data destruction industry, valued at USD 3.72 billion in 2025, is projected to reach USD 5.64 billion by 2029, according to research on secure data destruction market growth. This expansion is driven by businesses striving to comply with stringent data protection regulations and avoid becoming another cautionary tale.
For any organization handling sensitive information, professional data destruction is not optional—it's a fundamental responsibility. Failing to wipe a hard drive completely before disposal is like leaving your company’s front door unlocked.
Ultimately, knowing how to wipe a hard drive completely is about safeguarding your organization's future. It also integrates with broader corporate responsibilities, such as managing the environmental impact of electronic waste and ensuring a compliant and ethical IT asset disposition process.
Choosing Your Data Destruction Strategy
Selecting the appropriate method to wipe a hard drive is a strategic business decision that balances security requirements, compliance mandates, costs, and the lifecycle of your IT assets. Most organizations utilize a combination of two primary approaches: software-based wiping for asset reuse and physical destruction for ultimate data security. The key is knowing which method is appropriate for a given situation.
Before initiating any data destruction process, it is imperative to ensure all critical information is backed up and accessible. Having comprehensive backup and restore knowledge is a non-negotiable prerequisite. Once data is secured, you can proceed with permanent erasure.
This infographic illustrates the critical difference between standard deletion and secure wiping.
As shown, standard deletion creates a significant vulnerability because the data remains recoverable. A secure wipe, however, overwrites the data, rendering it permanently unrecoverable.
Software Wiping for Asset Redeployment
Software wiping is the optimal solution when you plan to reuse, sell, or donate hardware. This method uses specialized software to overwrite every sector of a hard drive with random data, making the original files forensically unrecoverable. It completely sanitizes the drive while preserving the functionality of the equipment.
This is the standard procedure for scenarios such as:
- Lease returns: Ensuring all proprietary data is eliminated before returning equipment to the leasing company is mandatory.
- Employee redeployment: It is the most secure method for preparing a computer for a new team member.
- Resale or donation: This allows you to recover value from your IT investment or support a charitable cause without exposing your company to data risk.
Adherence to recognized industry standards like DoD 5220.22-M (3-pass overwrite) and NIST 800-88 is crucial. Following these guidelines provides a defensible audit trail and demonstrates due diligence in protecting sensitive information.
Physical Destruction for Ultimate Security
When a drive is at its end-of-life, has failed, or contained highly sensitive information, physical destruction is the only acceptable method. This process ensures data can never be recovered because the storage media itself is physically obliterated.
For drives that stored your most critical assets—intellectual property, patient records, or confidential financial data—physical destruction is not just a best practice. It is the definitive line of defense against a catastrophic data breach. It offers zero ambiguity and zero chance of recovery.
The two most common methods are shredding and degaussing.
- Shredding: The hard drive is fed into an industrial shredder that grinds it into small metal fragments. It is the most widely used method due to its verifiable and visible outcome.
- Degaussing: A powerful magnetic field is used to neutralize the magnetic data on the drive's platters, instantly erasing all information and rendering the drive inoperable.
The demand for these fail-safe methods is increasing rapidly. The market for hard drive shredding services reached USD 0.72 billion in 2024 and is projected to grow to USD 1.2 billion by 2033. This growth is driven by regulated industries like healthcare and finance that require absolute certainty in data disposal.
Making the Right Choice for Your Business
The decision between software wiping and physical destruction comes down to a cost-benefit analysis based on the hardware's lifecycle stage and the sensitivity of the data it contained.
If the equipment has residual value, a software wipe is a secure and financially prudent strategy. However, for any drive that is obsolete, non-functional, or contained high-risk data, the absolute certainty of physical destruction is the only responsible choice.
For many businesses, partnering with a certified vendor is the most efficient and secure solution. Professional hard drive destruction services can manage both software wiping and physical shredding, providing essential documentation like Certificates of Destruction to prove compliance and protect your organization from liability. This allows you to focus on core business operations, confident that your data is being handled correctly.
Using Professional Software for In-House Data Wiping
For organizations with a dedicated IT department, performing data destruction in-house may seem like a cost-effective solution, particularly when repurposing equipment. This approach offers direct control over the process, but it also places the full weight of compliance risk and liability on your organization.
Executing this correctly requires professional-grade tools that are fundamentally different from the standard "format drive" command available in an operating system.
Specialized data erasure software is designed for one purpose: to permanently and completely destroy data, making it forensically unrecoverable. The industry-standard free tool for this is DBAN (Darik's Boot and Nuke). It is a powerful, self-contained application that boots from a USB drive to meticulously overwrite every sector of a hard drive.
Here is DBAN's classic, functional interface.
From this screen, you can select target drives and choose a wiping method to securely erase all data.
Preparing Your Bootable Wiping Tool
First, you must create bootable media. Download the ISO file for a tool like DBAN or a commercial alternative and use a utility such as Rufus or balenaEtcher to write it to a USB flash drive. This transforms the USB drive into a dedicated, self-contained data destruction operating system.
This process is analogous to using a master key for a vehicle. By booting a computer from this USB drive, you bypass the machine's installed OS (e.g., Windows or macOS). This provides the wiping software with unrestricted access to erase the primary system drive without interference from the operating system.
Executing the Wipe with Precision
After booting from the USB, the software will display a list of all connected hard drives. This is a critical step that requires extreme caution, as a mistake can lead to catastrophic data loss. You must be absolutely certain you have identified the correct drive for erasure.
Pro-Tip: Before beginning, disconnect any external drives or network storage that are not intended for erasure. On servers with multiple drives, physically verify serial numbers or use the BIOS to confirm you are targeting the correct device. Wiping the wrong drive is an irreversible error.
After selecting the target drive(s), you will choose an erasure method. Common options include:
- Quick Erase: A single pass that overwrites the drive with zeros. Suitable for low-risk, internal repurposing.
- DoD 5220.22-M: The standard 3-pass method that writes patterns of ones, zeros, and random characters. This is a widely accepted standard for corporate data sanitization.
- PRNG Stream: A single pass that writes cryptographically secure pseudo-random data across the drive.
For most business applications, the DoD 3-pass wipe provides an optimal balance of security and efficiency, defeating all but the most sophisticated laboratory recovery techniques.
The objective is not merely to delete files but to obliterate the original data so completely that no trace remains. A multi-pass overwrite ensures that even faint magnetic signatures, known as "data remanence," are effectively scrambled beyond recognition.
The Overlooked Steps: Verification and Logging
This is where many in-house data wiping initiatives fall short, creating significant business risk. Executing the wipe is not sufficient. For compliance and liability protection, you must prove the wipe was successful.
-
Run a Verification Pass: After the overwrite process is complete, the software should perform a read-pass on every sector to confirm it contains only the new, random data. This verifies that the wipe was 100% successful and no bad sectors were missed. A failed verification means the drive cannot be considered securely wiped.
-
Generate Detailed Logs: This is your audit trail. Professional-grade software will generate a detailed report for each wiped drive. This log must include the drive's serial number, the erasure standard used, the exact date and time, and the verification result.
These two final steps distinguish a casual format from a defensible, enterprise-grade data destruction process. Without verification and logs, you have no evidence that the data was destroyed, leaving your organization exposed during an audit or legal proceeding. A truly comprehensive approach to your company's data security demands this level of documentation.
When Your Operating System's Built-In Tools Make Sense
While dedicated software provides the gold standard for security and an audit trail, not every situation requires that level of rigor. For low-risk, internal-only scenarios—such as reassigning a workstation to a new employee—the data sanitization tools built into Windows and macOS can be a practical choice.
These tools are convenient and free, eliminating the need to create bootable media or install new software. However, it is critical to understand their appropriate use cases and limitations.
Wiping a Drive with Windows Tools
Modern versions of Windows include a feature called "Reset this PC." It is designed to restore the system to a clean state and offers a basic level of data sanitization that is superior to simple file deletion.
During the process, Windows presents a critical choice: "Keep my files" or "Remove everything." For any data sanitization purpose, you must select "Remove everything." This reformats the drive and reinstalls a fresh copy of Windows. Newer versions of Windows 10 and 11 also offer a "Clean data" option, which performs a single-pass overwrite to make data recovery more difficult.
For command-line users, the format command in Command Prompt or PowerShell remains available. A command like format D: /P:1 will format the D: drive and perform a single pass of zeros over every sector. While more secure than a standard format, it does not meet the standards of professional multi-pass utilities.
Using Disk Utility on macOS
Apple provides a similar tool in its Disk Utility application. To erase a drive on a Mac, Disk Utility offers "Security Options" that allow you to control the thoroughness of the data overwrite. The options range from a fast, single-pass erase to more secure multi-pass wipes.
To erase the main system drive, you must boot into Recovery Mode. From there, launch Disk Utility, select the target drive, and click "Erase." A "Security Options" slider will appear, allowing you to select a more secure, multi-pass erase, which is sufficient for internal redeployment.
Consider these built-in OS tools as the digital equivalent of shredding a routine internal memo. They are suitable for low-stakes tasks, but they should not be trusted for destroying documents containing your company's most sensitive information.
The Critical Limitations for Business Use
It is imperative to understand that built-in OS tools are not a substitute for enterprise-grade data destruction. They are suitable for preparing a machine for internal transfer but are inadequate for ensuring business compliance and mitigating liability.
- No Certification: These tools do not generate a Certificate of Destruction. There is no official, auditable proof that the wipe was completed successfully to a recognized standard.
- Limited Standards: They generally do not offer advanced wiping patterns like the DoD 5220.22-M 3-pass standard, which is often a minimum requirement for corporate data policies.
- No Centralized Management: Wiping machines individually is a manual, inefficient process that does not scale for large-scale IT asset decommissioning projects.
- Compliance Gaps: Relying on these methods is insufficient for meeting regulatory requirements like HIPAA, GDPR, or CCPA. An auditor will identify this as a significant gap in your data security protocol.
In summary, these tools offer convenience, not compliance. For any hardware leaving your organization's control—whether for resale, recycling, or donation—a more robust and verifiable process is required. When you donate a laptop or other IT assets, using a certified service that provides proof of destruction is the only way to fully protect your organization.
Verification and Compliance: The Final Step
Wiping a hard drive is more than a technical procedure; it is a critical business function. For any organization, the process is not complete until you can prove, with certainty, that the data has been rendered unrecoverable. This final step—verification and compliance—is what distinguishes a secure, defensible process from a significant liability.
Regulations such as GDPR, HIPAA, and CCPA require not only that you protect data but also that you can demonstrate due diligence. In the event of an audit or legal challenge, a statement like "we are confident it was wiped" is insufficient. You need an airtight, auditable record confirming that every data-bearing asset was properly sanitized or destroyed.
This is where verifiable proof becomes non-negotiable. Without it, your business remains exposed to severe financial penalties and reputational harm, even if the wipe was performed correctly.
The Power of a Certificate of Destruction
The most critical document in your data disposal protocol is the Certificate of Destruction (CoD). This is not merely a receipt; it is a legal document that serves as your official proof of compliance. It formally transfers liability for data destruction from your organization to the certified vendor who performed the service.
A legitimate CoD is detailed and specific. To withstand audit scrutiny, it must include:
- Unique Serial Numbers: A complete inventory of every hard drive or asset that was destroyed.
- Method of Destruction: A clear statement on how the data was destroyed (e.g., DoD 5220.22-M 3-pass wipe, physical shredding).
- Chain of Custody: Records of who handled the assets, the location of handling, and the exact date of completion.
- Official Signature: A signature from an authorized representative of the certified data destruction vendor.
This document is your ultimate safeguard. When an auditor inquires about the disposal of a specific server from five years prior, you can produce the CoD to demonstrate precisely when and how its drives were professionally and permanently sanitized.
Choosing a Certified Partner for Peace of Mind
While in-house wiping is an option, partnering with a certified vendor is the most secure and legally defensible strategy for most businesses. Look for vendors with credentials like NAID AAA Certification, the gold standard for secure data destruction. This certification confirms that the vendor's entire process—from employee screening to facility security—has been rigorously audited by an independent third party.
By engaging a certified data destruction partner, you're not just outsourcing a task—you are strategically transferring risk. Their expertise and documentation become your shield, ensuring your company's data disposal process is legally defensible and compliant with the highest industry standards.
The rapid growth of the data destruction service market reflects its importance. It was valued at USD 1.5 billion in 2024 and is projected to reach USD 3.2 billion by 2033. This growth is driven by businesses in regulated sectors like healthcare and finance that recognize the absolute necessity of certified, secure disposal. You can learn more about the data destruction service market to understand its critical role.
Ultimately, compliance is a core component of your equipment's entire lifecycle. For a comprehensive overview of managing end-of-life hardware, see our guide on what is IT asset disposition, which details how to integrate verification and compliance into your overall strategy.
Frequently Asked Questions About Wiping Business Hard Drives
Even with a well-defined policy, IT managers and business leaders often have questions regarding the disposal of old hard drives. Addressing these common concerns is crucial for mitigating organizational risk. This section serves as a quick-reference guide to reinforce key concepts.
Does a Standard Format Really Wipe a Hard Drive?
No, absolutely not. This is one of the most dangerous misconceptions in corporate data security.
A standard format only removes the file address table—the "table of contents" for your data. The actual files remain fully intact on the drive, merely hidden from the operating system. Anyone with widely available, often free, recovery software can easily reconstruct this sensitive information.
For any business asset, this constitutes an unacceptable risk. A secure wipe is fundamentally different; it overwrites every sector of the drive with random data, permanently destroying the original information and rendering it forensically unrecoverable.
How Do I Decide Between Software Wiping and Physical Destruction?
The appropriate choice depends on two factors: the asset's residual value and the sensitivity of the data it contained. This is a strategic business decision, not merely a technical one.
- Use Software Wiping for hardware you intend to reuse, resell, or donate. This method preserves the physical drive, allowing you to recover value from your IT assets while ensuring complete data sanitization. It is the ideal approach for managing the lifecycle of functional equipment.
- Choose Physical Destruction for drives that are non-functional, obsolete, or contained your company's most critical data. Shredding provides absolute certainty that the data can never be recovered. It is often the mandated method for compliance in regulated industries like healthcare (HIPAA) and finance.
What Is a Certificate of Destruction and Why Is It So Important?
A Certificate of Destruction is a formal document provided by a certified vendor that serves as legal proof that your data-bearing assets were destroyed in accordance with industry standards. It is not just a receipt—it is your official audit trail.
This document is your primary defense in a compliance investigation, as it includes:
- A list of asset serial numbers
- The specific destruction method used
- Chain of custody details (who handled the assets and when)
- The date and location of the destruction
During an audit, a Certificate of Destruction demonstrates your company's due diligence. It effectively transfers the liability for proper data disposal to the vendor, protecting you from the significant fines and legal consequences associated with regulations like GDPR or HIPAA.
Is It Safe to Have Our Own IT Team Wipe Our Hard Drives?
While an internal IT team possesses the technical skills to operate wiping software, an in-house process creates significant business risks. It is often slow, requires specialized expertise to verify success across diverse hardware types, and, most importantly, it generates no independent, third-party audit trail.
For any organization concerned with compliance and liability, engaging a certified, independent vendor is the most prudent and secure strategy. You receive third-party verification that the process was executed correctly and the essential Certificate of Destruction as proof. This approach transfers risk, ensures a legally defensible disposal process, and allows your IT team to focus on core operational responsibilities.
When it's time to retire your company's IT assets, don't leave data security to chance. At Atlanta Computer Recycling, we provide certified, secure, and compliant data destruction services for businesses across the Atlanta metro area. We handle everything from on-site pickup to providing the official Certificate of Destruction you need for total peace of mind.
Protect your business and ensure your compliance by visiting us at https://atlantacomputerrecycling.com.