How to Dispose of Old Computers Safely: A Guide for Businesses

When your business is ready to retire old IT assets, the process is far more complex than just unplugging a server. A proper IT asset disposition plan starts with a verified data backup, moves on to certified data destruction to eliminate any chance of recovery, and finishes with environmentally compliant recycling through a professional partner. This isn't just about clearing out a storage room—it’s about protecting your business from data breaches, regulatory fines, and reputational damage.
Why Safe Computer Disposal Is a Business Imperative
That old server or stack of laptops might look like harmless clutter, but for a business, each device is a potential liability. How you handle its final send-off isn't just an IT chore. It's a critical function tied directly to your company's security, reputation, and even its financial health.
Ignoring a secure disposal process is like leaving your company's digital front door wide open. Imagine a competitor—or worse, a cybercriminal—getting their hands on a hard drive your IT team thought was wiped clean. Suddenly, your sensitive financial records, client lists, or proprietary trade secrets are exposed. The fallout can be devastating, from massive data breaches and non-compliance fines to a total collapse of customer trust.
The Real Costs of Improper Disposal
The consequences of getting IT asset disposal wrong are very real and very expensive. Beyond the immediate threat of data theft, businesses are entangled in a complex web of regulations. Failing to meet these standards isn't just an oversight; it's a significant liability that can impact your bottom line.
Here’s what your business is up against:
- Regulatory Penalties: Data privacy laws like HIPAA and GDPR come with staggering fines for non-compliance, often running into the millions of dollars.
- Legal Action: A data breach traced back to an improperly discarded computer can easily trigger costly lawsuits from customers and partners whose information was compromised.
- Brand Damage: News of a data leak can permanently damage your reputation, scaring off both current and potential customers for good.
- Environmental Non-Compliance: Illegally dumping e-waste leads to hefty fines and public backlash. The environmental impact of electronic waste is a growing concern, and regulators are cracking down.
A common, high-risk mistake we see is companies relying on a simple factory reset or drive format. The truth is, data from formatted drives can often be recovered with easily available software. This simple slip-up can quickly become a company's most expensive lesson.
A Strategic Approach to IT Asset Disposition
It's time for businesses to stop thinking about this as "disposal" and start seeing it as a strategic process. The industry term for this is IT Asset Disposition (ITAD), and it reframes the task from a simple cleanout to a structured risk management protocol. A solid ITAD strategy isn't just an expense—it's an investment in your company's operational integrity.
Understanding the bigger picture of risk and compliance management helps clarify why this is so important. A professional ITAD partner doesn't just take your old gear; they provide essential documentation, like Certificates of Destruction, that prove you followed compliant procedures. In the event of an audit, that paperwork is your proof of due diligence. This strategic mindset turns a potential disaster into a secure, verified, and compliant business process that protects your bottom line.
Don't Let Data Walk Out The Door: Mastering Corporate Data Destruction
Before a single corporate computer leaves your facility—whether for recycling, donation, or resale—you must deal with the data on its hard drive. Hitting 'delete' or performing a quick reformat is a rookie mistake that leaves your company wide open to risk. This is the absolute most important step in the entire disposal process. For a cybercriminal, a recoverable hard drive is a goldmine.
True professional data destruction isn't about just deleting files. It's about making them completely, permanently, and verifiably unrecoverable. This is your first line of defense against a data breach and a non-negotiable part of staying compliant with privacy laws.
Let's break down the industry-standard methods that ensure your sensitive corporate information is gone for good.
The Digital Scrub: Software-Based Data Wiping
Software-based wiping is one of the most common and effective ways to sanitize a hard drive for business use. It doesn't just delete your files; it uses specialized software to write over every single sector of the drive with random, meaningless data. Think of it as systematically burying the old information under layers of digital gibberish.
The key is to use software that meets recognized standards. The NIST 800-88 guidelines, published by the National Institute of Standards and Technology, are the gold standard for media sanitization. Following this protocol ensures the job is done right and you can prove it. We get into the nitty-gritty of this process in our guide on how to properly wipe a hard drive.
For most businesses, especially those in healthcare or finance dealing with regulations like HIPAA or GDPR, using a certified vendor for NIST-compliant wiping is a must. You get a Certificate of Data Destruction, which is your legal proof that you performed your due diligence.
The Magnetic Zap: When to Use Degaussing
For older magnetic storage like traditional hard disk drives (HDDs) and backup tapes, degaussing is an incredibly powerful option. A degausser is an industrial machine that unleashes a massive magnetic field, instantly scrambling the magnetic structure of a drive where data is stored.
The process is lightning-fast and extremely effective, but there's a catch: it completely destroys the hard drive, rendering it unusable. Degaussing is perfect for destroying large volumes of old drives that are at the end of their life and have no resale value. Just remember, this method is useless on Solid-State Drives (SSDs), which store data electronically, not magnetically.
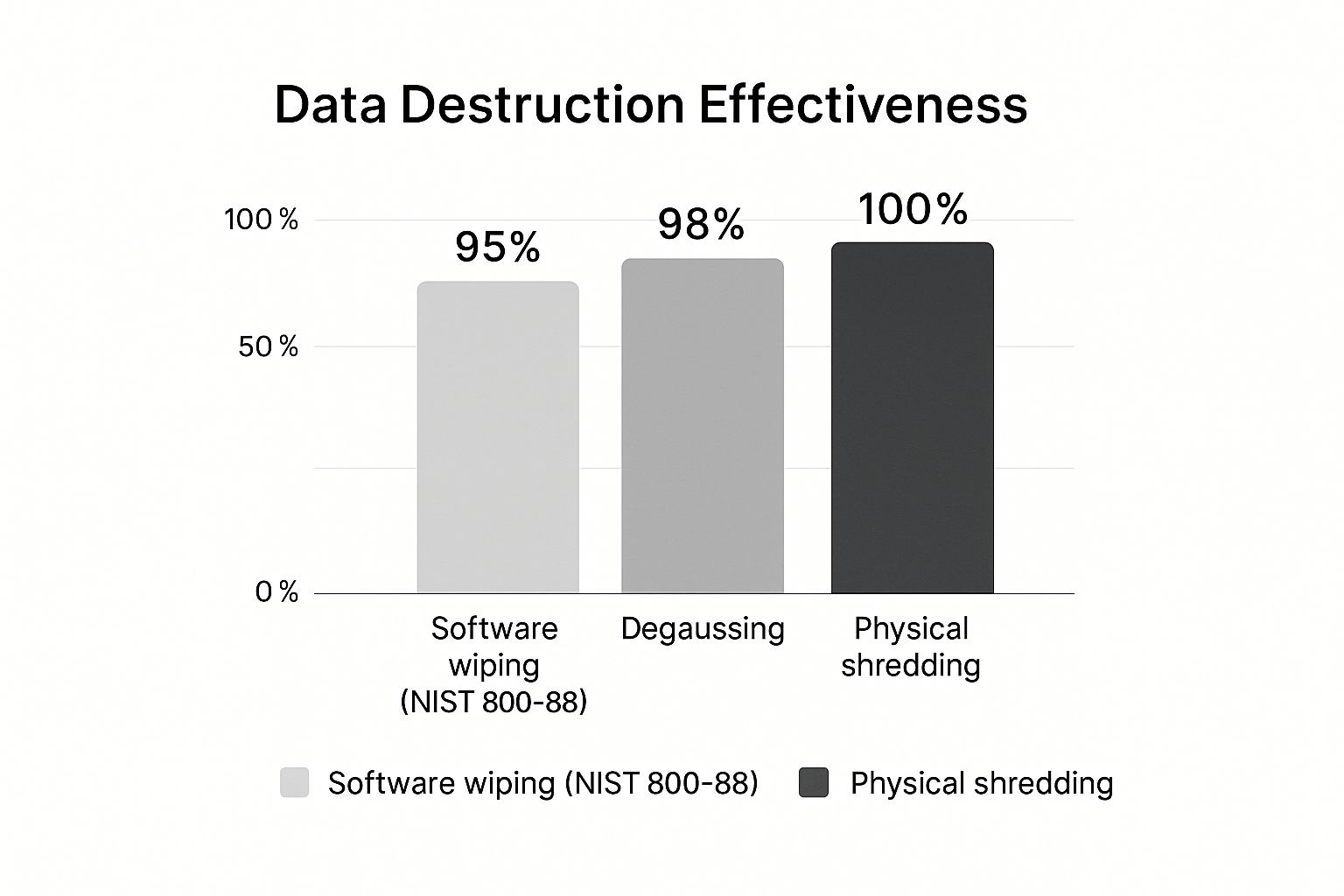
This infographic gives you a quick visual on how the different methods stack up.
As you can see, software wiping is incredibly secure, but only physical destruction offers a 100% guarantee that data is gone forever.
The Final Word: Physical Destruction
When you need absolute certainty that data can never be recovered—no ifs, ands, or buts—physical destruction is the only way to go. This means feeding hard drives, SSDs, and other media into an industrial-grade shredder that grinds them into tiny fragments of metal and plastic.
There is no coming back from this. No technology on earth can piece that data back together once a drive has been turned into confetti. This is the standard for government agencies, financial institutions, and healthcare organizations with top-secret or highly sensitive data. It’s the ultimate peace of mind for corporate data security.
So, how do you choose the right method for your business needs?
- Software Wiping (NIST 800-88): Your best bet for drives you plan to reuse, donate, or resell. It keeps the hardware intact while erasing the data.
- Degaussing: A great choice for getting rid of large batches of old HDDs quickly when you don't care about salvaging the hardware.
- Physical Shredding: The ultimate solution for maximum-security scenarios. It's often required for top-secret information and is the only surefire way to destroy SSDs.
Picking the right method is more than just a technical choice; it’s a core part of your risk management strategy. It’s also an environmental one. The United Nations has flagged e-waste as a massive global problem, with old computers leaching toxic materials into our soil and water. A single computer monitor can contain up to 8 pounds of lead. By working with a certified recycler for both data destruction and disposal, you can meet your obligations for security and environmental stewardship.
Choosing Your Disposal Path: Recycling, Resale, or Donation?
Once you’ve guaranteed every last byte of company data has been professionally destroyed, your attention can shift to the physical hardware. What do you do with all those old machines? This isn’t just about cleaning out a closet; it's a strategic decision that affects your bottom line, security posture, and even your public image.
For any business, getting rid of old computers safely comes down to three main options: certified e-waste recycling, IT asset remarketing (resale), or corporate donation. Each path has its own set of benefits and potential pitfalls. Getting it right means turning a potential liability into a well-managed asset.
The Certified Recycling Route for Ultimate Security
For most businesses, especially those in highly regulated fields like healthcare or finance, certified e-waste recycling is the safest and most common choice. This path puts security and compliance above everything else. When you bring in a certified recycler, you're not just tossing out old gear—you're hiring a professional service to responsibly dismantle it according to strict environmental and data security standards.
The biggest win here is risk mitigation. A certified partner provides an auditable paper trail, including Certificates of Recycling and Destruction. This is your legal proof of due diligence, and it's invaluable if an auditor comes knocking. While you won't see a financial return on obsolete assets, the peace of mind is priceless. A great first step is to get familiar with local electronic waste recycling services to see how a compliant program works.
Tapping into Resale for Financial Return
What if your equipment isn't obsolete? If you're refreshing laptops, servers, or networking gear that's only two or three years old, then resale—or IT asset remarketing—is a fantastic option. This approach can turn your retired hardware into a new revenue stream, helping to offset the cost of new technology.
The process usually involves a specialized ITAD vendor. They’ll assess your assets, perform certified data destruction, and then refurbish and sell the equipment through their network. They handle all the heavy lifting—testing, cleaning, marketing—and provide a share of the profits.
The key here is choosing your partner carefully. The chain of custody is everything. You need a vendor who can provide crystal-clear reporting on every single device and guarantee data sanitization before anything is resold.
Strategic Donations for Community Impact and Tax Benefits
Donating functional but older computers to schools or non-profits is a great way to support the community and boost your company's Corporate Social Responsibility (CSR) profile. It’s a move that feels good, looks great in the public eye, and can even offer tax deductions.
But just like with resale, the data security responsibility is 100% yours. Before a single computer leaves your facility, you must ensure its drive has been professionally wiped using a standard like NIST 800-88. It's a huge mistake to assume the receiving organization will handle it—that liability doesn't transfer with the hardware.
It's also a good idea to partner with organizations that have a plan for the equipment's eventual end of life. You don't want your well-intentioned donation to end up in a landfill a few years later, creating a negative story that traces right back to your business.
Comparing Business Computer Disposal Methods
To help you decide which path makes the most sense for your business goals, we've broken down the key factors in this table.
| Disposal Method | Best For | Key Benefit | Primary Risk | Compliance Factor |
|---|---|---|---|---|
| Certified Recycling | Older, non-functional, or data-sensitive equipment | Bulletproof security and compliance documentation | No financial return on assets | Highest level of auditable compliance |
| IT Asset Resale | Newer equipment (under 3-4 years old) with market value | Potential for significant financial ROI | Data breach if partner's process is weak | Requires strict chain of custody and verified data wiping |
| Corporate Donation | Functional equipment that is no longer needed internally | Positive CSR impact and potential tax deductions | Data liability remains with your company | Demands rigorous, verified data destruction prior to donation |
In reality, many companies find a hybrid approach works best. Newer, high-value assets go into a remarketing program, older and broken devices are sent for certified recycling, and a select batch of functional machines is prepared for a structured donation program. This balanced strategy helps you get rid of old computers safely while maximizing value and upholding all your corporate responsibilities.
Selecting a Certified IT Asset Disposition Partner
Choosing your IT Asset Disposition (ITAD) partner is probably the single most critical decision you'll make in this entire process. This goes way beyond just finding someone to haul away old equipment. The right partner is the final, crucial link in your data security chain, and getting it wrong can instantly unravel all your internal efforts.
A non-certified vendor might offer a temptingly low price, but the risks are massive. We've seen firsthand what can happen. One healthcare provider hired a local "e-waste collector" to dispose of old patient computers. That vendor illegally dumped the machines in a landfill—with patient data still on them. The result was a devastating HIPAA fine and a public relations disaster.
It's a brutal lesson: your company's liability doesn't walk out the door when the computers do.
Decoding Key Industry Certifications
When you're vetting potential ITAD partners, don't think of certifications as just fancy badges for their website. They are your proof of a secure, compliant, and audited process. They show that a vendor has subjected their operations to rigorous third-party scrutiny and meets the highest industry standards for handling both data and e-waste.
Here are the certifications you absolutely need to see:
- R2 (Responsible Recycling): This certification is focused on protecting the environment, workers, and your data. An R2-certified recycler is audited to ensure they follow a strict hierarchy: reuse first, then recycling, and finally responsible disposal.
- e-Stewards: Often considered the gold standard for environmental protection, e-Stewards certification strictly forbids exporting hazardous e-waste to developing countries. It’s your best guarantee that your old equipment won’t create a toxic mess overseas.
- NAID AAA Certification: This certification is laser-focused on data destruction. A NAID AAA-certified vendor has been thoroughly audited on their data sanitization processes, employee screening, and facility security. It’s the ultimate assurance that your corporate data is handled and destroyed correctly.
Choosing a partner holding these certifications isn’t just a good idea—it's non-negotiable. It's your first and best line of defense, proving you’ve done your due diligence to protect your company's sensitive information. A vendor without them is a massive blind spot in your security strategy.
Essential Questions to Ask a Potential ITAD Partner
Once you've narrowed your list down to certified vendors, it's time to dig deeper. How they answer these questions will tell you everything you need to know about their real-world capabilities. You need a partner who provides a clear, auditable trail from start to finish.
Before you sign a service agreement, get solid answers to these questions:
- Can you provide a complete, serialized chain of custody? They need to track every single asset from the moment it leaves your building to its final disposition. Vague "group logs" aren't good enough.
- How do you verify data destruction? Ask to see a sample Certificate of Data Destruction. It must detail the method used (e.g., NIST 800-88 wipe, physical shredding) and list the serial numbers of the destroyed drives.
- Do you audit your downstream vendors? Your ITAD partner might use other companies for things like smelting or final material recovery. You need confirmation that they vet and audit those downstream partners to the same tough standards.
- What are your on-site and transit security protocols? How are assets secured during transport? Are their vehicles tracked? Are their employees background-checked and clearly identifiable?
- Can we witness the destruction process? Reputable vendors won't hesitate. They should allow you to watch the physical shredding of your drives, either in person or via a secure video feed, for total peace of mind.
While vetting an ITAD partner involves very specific criteria, the basic principles of choosing a reliable service company are the same. For some broader tips, you may find this piece offering general guidance on choosing a trustworthy service provider useful.
Taking the time to properly vet your partner is the final, essential step in disposing of old computers safely. It’s how you turn a potential liability into a secure, documented, and compliant success.
Building Your Internal IT Disposal Policy
A solid plan for disposing of old computers safely doesn’t just happen—it’s the result of a clear, documented, and repeatable internal process. You can't just hand everything off to your ITAD partner and hope for the best. What your business needs is a formal corporate IT Asset Disposal (ITAD) policy that takes the guesswork out of the equation, standardizes your procedures, and makes sure every employee knows their role in protecting company assets.
Think of this policy as your internal rulebook. It creates a framework that guarantees consistency and seriously cuts down on the risk of human error. It’s also your best defense in an audit and a powerful way to show regulators you’re performing your due diligence. Without one, you're leaving your company's security to chance.
Core Components of a Rock-Solid ITAD Policy
A truly comprehensive ITAD policy is way more than a simple checklist. It needs to map out the entire lifecycle of an asset, from the day it's purchased to its final, verified destruction. This document should be easy for all relevant staff to find and understand, from the IT admins managing the hardware to the department heads signing off on equipment upgrades.
Your policy must spell out the following areas in no uncertain terms:
- Asset Tracking Protocols: Mandate a system for logging every single piece of hardware. This means capturing serial numbers, assigned users, and deployment dates to create an unbroken chain of custody long before an asset is ever retired.
- Data Sanitization Standards: Get specific about the exact data destruction methods required for different types of data and hardware. For example, all laptops with client data must undergo a NIST 800-88 compliant wipe. Meanwhile, drives from decommissioned servers that handled financial records require physical shredding. No exceptions.
- Employee Responsibilities: Clearly outline who is responsible for what. Define who has the authority to approve a disposal, who manages the physical inventory, and who is the main point of contact for your certified ITAD partner.
- Documentation Requirements: Make it mandatory to get—and archive—all disposal-related paperwork. This includes chain of custody forms, Certificates of Data Destruction, and Certificates of Recycling for every single batch of assets.
Your policy isn't just about ticking compliance boxes; it's about building a culture of security. When every team member understands the 'why' behind the rules—to protect client data and the company's reputation—they become active defenders of your security posture.
Maintaining Meticulous Records for Audits
Picture this: a regulator is asking about your disposal practices from two years ago. Can you pull up the exact serial numbers of the hard drives that were destroyed and the certificate to prove it? With a strong policy in place, the answer is a confident "yes." Meticulous record-keeping is your ultimate safeguard.
Your ITAD partner will provide the critical documents, but your policy must dictate how they are stored, who can access them, and for how long they need to be kept. This auditable trail is proof that you didn't just cross your fingers and hope for the best; you verified every single step. For businesses that need to meet strict compliance mandates, our detailed guide on enterprise data security offers deeper insights into building these safeguards.
Connecting Disposal to Corporate Sustainability Goals
A robust ITAD policy does more than protect your data; it reinforces your company’s commitment to corporate social responsibility. By formalizing your partnership with a certified e-waste recycler, your policy becomes a tangible expression of your environmental goals. This is more important than ever, given the global e-waste crisis.
Globally, a staggering 82.6% of electronic waste is not properly collected or recycled. That means millions of tons of hazardous materials are dumped in landfills each year. To get a better sense of the scale of this challenge, you can explore the latest global e-waste statistics and findings.
By mandating certified recycling in your policy, you ensure your company is part of the solution, not the problem. This strengthens your brand reputation and aligns your IT operations with broader sustainability initiatives that customers and stakeholders truly care about.
Common Questions About Computer Disposal
When it comes to getting rid of old IT assets, businesses often have a lot of the same questions. Let's tackle some of the most common ones we hear, clearing up the confusion around secure and compliant computer disposal.
Is Just Reformatting Our Office Hard Drives Good Enough?
I hear this one a lot, and the answer is a hard no. Thinking a simple reformat is enough to protect your data is one of the most dangerous mistakes a company can make.
All reformatting does is remove the pointers to your files, kind of like tearing the table of contents out of a book. The actual chapters—your sensitive company and client data—are still sitting right there on the drive, easily recoverable with off-the-shelf software.
For any business, but especially one handling data covered by regulations like HIPAA or GDPR, this is a data breach waiting to happen. The only way to be certain your data is gone for good is to use professional-grade data wiping software that meets a standard like NIST 800-88, or even better, go for the absolute finality of physical shredding.
What Kind of Paperwork Should I Get From My Disposal Vendor?
Vague promises and a handshake won't cut it. A professional ITAD partner will provide a complete, auditable paper trail that proves you did everything right. If your vendor can't provide this, find a new one.
You should always walk away with these key documents:
- A Certificate of Data Destruction: This is your official proof that the data on your devices was permanently destroyed. It should be detailed, listing the serial numbers of the drives and the exact destruction method used.
- A Certificate of Recycling: This document verifies that the physical hardware was dismantled and processed in an environmentally compliant way, following all e-waste regulations.
- A Full Chain of Custody Record: This tracks your assets from the second they leave your office to their final destruction or recycling, ensuring nothing gets "lost" along the way.
Without this paperwork, you have zero verifiable proof that your company’s data was securely managed or that you disposed of e-waste responsibly. In an audit, these documents are your best defense.
Can We Just Donate Our Old Computers To a School or Charity?
Donating equipment to a local school or nonprofit is a fantastic way to give back to the community, but it doesn't get you off the hook for data security. Your legal responsibility for the data on those machines remains squarely with you.
This means you absolutely must ensure every single storage device is professionally wiped or physically destroyed by a certified partner before it ever leaves your control. Giving away a computer doesn't transfer your liability. It's also a smart move to check that the organization you're donating to has a responsible plan for when the hardware eventually reaches its end of life—protecting your company’s reputation down the road.
What's the Real Difference Between R2 and E-Stewards?
Both R2 (Responsible Recycling) and e-Stewards are the gold standards in certified, responsible electronics recycling. They're both great, but they operate on a slightly different philosophy, and it's worth knowing the distinction.
The e-Stewards standard, which was created by the environmental group Basel Action Network, has a strict, zero-tolerance policy against exporting hazardous e-waste to developing countries. Period.
The R2 standard, on the other hand, does permit the export of tested, functioning equipment under certain legal conditions. For businesses that want the absolute highest level of assurance against environmental and reputational risks, e-Stewards is generally considered the most rigorous global standard.
At Atlanta Computer Recycling, we provide the certified, secure, and documented ITAD services your business needs to dispose of old equipment with complete confidence. Contact us today to schedule your secure electronics pickup.