Your Guide to Commercial Atlanta Electronics Recycling

For any business in Atlanta, treating electronics recycling as mere "disposal" is a significant strategic error. It's an exercise in risk management. A comprehensive, professionally managed IT Asset Disposition (ITAD) strategy is the critical barrier between your organization and the catastrophic financial and reputational costs of a data breach or compliance failure.
Why Your Business Must Prioritize Electronics Recycling
When servers, laptops, and hard drives reach their end-of-life, they don't just occupy storage space. They become active liabilities. Every device represents a potential data breach waiting to happen, loaded with sensitive corporate financials, customer PII, or proprietary trade secrets. Simply hitting "delete" or, worse, discarding old equipment in a dumpster is an open invitation to a security disaster.
Here's the critical challenge for Georgia businesses: the state lacks specific e-waste laws mandating commercial recycling. This regulatory gap places the entire burden of responsible disposition squarely on your company. Without state mandates, federal regulations like HIPAA for healthcare or FACTA for financial institutions become the governing standard, and they demand ironclad, verifiable proof of secure data destruction.
Protecting Your Bottom Line and Reputation
The consequences of improper IT asset disposition are severe. A single data breach can spiral into millions of dollars in regulatory fines, litigation, and mandatory customer notifications. The damage to your brand’s reputation, however, can be far more costly and take years to repair, eroding the customer trust you've worked diligently to build.
This is precisely where a professional Atlanta electronics recycling partner becomes an essential business function. They don't just haul away old equipment; they provide a secure, documented process that transforms a major operational liability into a streamlined, compliant procedure. A certified ITAD vendor guarantees that every data-bearing device is handled securely from the moment it leaves your facility.
A formalized ITAD program is no longer a "nice-to-have"; it's a core component of corporate governance. It's about proactively managing risk, ensuring compliance, and protecting the critical information that drives your business.
It's More Than Just Disposal—It's Strategic Asset Management
Viewing ITAD as just "getting rid of old stuff" overlooks its strategic value. A well-executed program delivers significant benefits beyond ticking a compliance box. It’s a comprehensive plan for managing retired assets in a way that is secure, environmentally responsible, and financially prudent.
A professional ITAD strategy will always include:
- Data Security: Employing certified data destruction methods that make sensitive information physically irrecoverable.
- Compliance: Providing legally defensible documentation, such as Certificates of Destruction, to prove you met all regulatory requirements.
- Environmental Responsibility: Ensuring hazardous materials are managed correctly and valuable resources are recovered, addressing the growing public concern over the environmental impact of electronic waste.
- Logistical Efficiency: Managing the on-site de-installation, packing, and transportation of assets with minimal disruption to your daily operations.
This guide is a strategic roadmap for Atlanta's IT managers, compliance officers, and business leaders. We will walk you through the essential steps—from creating a detailed inventory and selecting a certified partner to understanding data destruction protocols and planning a seamless, secure pickup.
Creating Your IT Asset Disposition Inventory
Before you can schedule a secure pickup or receive an accurate quote, you must know exactly what assets you are retiring. A detailed IT asset inventory isn't just a best practice; it's the foundation of any successful Atlanta electronics recycling project. This process is about more than just counting computers—it's about creating an auditable record that shields your business from risk.
This inventory serves as the blueprint for your entire disposition process. It simplifies logistics, guarantees every data-bearing device is accounted for, and can even identify assets that retain resale value. Without it, you are operating with a critical blind spot in your security protocol.
What to Track for Every Corporate Asset
To build an effective inventory, you must capture specific data points for each device. The objective is to create a clear, detailed list that your ITAD partner can use to scope the project, from data destruction requirements to transportation logistics.
Your spreadsheet or asset management software should track several key fields for every item slated for disposition. This detail is what transforms a simple list into a powerful compliance tool.
Here’s what you must record for each item:
- Asset Tag or Serial Number: This is the non-negotiable unique identifier for establishing an auditable chain of custody.
- Device Type: Be specific. Is it a Dell PowerEdge R740 server, a Lenovo ThinkPad T14 laptop, or a Cisco Catalyst 9300 switch? The details are critical for planning.
- Physical Location: Note the floor, room number, or data center rack. This information is crucial for efficient physical removal.
- Data-Bearing Status: This is the most critical field. A simple "Yes" or "No" flags every device that requires certified data destruction.
While this may seem overly detailed for old equipment, it is essential for demonstrating due diligence. It proves you have taken a methodical approach to tracking and securing every potential source of a data breach.
From Data Center Hardware to Loose Media
Your inventory must be comprehensive, covering everything—not just obvious assets like laptops and desktops. Often, the highest-risk items are those overlooked in a storage closet or a forgotten corner of the server room.
Do not overlook these common but critical assets:
- Network Gear: Routers, switches, and firewalls often store sensitive network configurations and access credentials.
- Loose Media: Individual hard drives (HDDs), solid-state drives (SSDs), and backup tapes are pure data and must be inventoried meticulously.
- Mobile Devices: Company-issued smartphones and tablets contain a high concentration of sensitive corporate data.
The core principle is simple: if it was powered on and could store company data, it requires a line item on your inventory. This meticulous approach is the first line of defense in a compliant ITAD strategy.
To streamline this process, use the following checklist to ensure you capture the right information for each asset class.
IT Asset Inventory Checklist for Secure Disposition
This table breaks down the essential data points you need to capture to ensure a secure and compliant disposition process for various types of IT hardware.
| Asset Category (e.g., Server, Laptop, Hard Drive) | Key Information to Record | Data Security Consideration | Potential for Reuse? |
|---|---|---|---|
| Servers | Make, Model, Serial #, # of HDDs/SSDs, Location (Rack #) | High-risk. Contains business-critical and sensitive data. | Yes, if modern and functional. |
| Laptops/Desktops | Make, Model, Serial #, Asset Tag, HDD/SSD type and size | High-risk. Often contains user data, credentials, and PII. | Yes, high potential if less than 5 years old. |
| Loose Hard Drives (HDD/SSD) | Serial #, Capacity, Type (SATA, SAS, NVMe) | Extreme-risk. Pure data storage requiring physical destruction. | No. Best practice is to shred. |
| Networking Gear (Switches, Routers) | Make, Model, Serial #, Port Count | Medium-risk. Can store network configurations and credentials. | Yes, for enterprise-grade equipment. |
| Mobile Devices (Phones, Tablets) | Make, Model, IMEI/Serial #, Asset Tag | High-risk. Contains PII, emails, and company app data. | Yes, depending on model and condition. |
Using a structured checklist ensures no device is overlooked, protecting your organization from potential data breaches.
Creating this inventory is also an ideal time to align with other major business initiatives. For instance, if you're undertaking a professional office decommissioning, integrating your ITAD inventory from the outset streamlines the entire project. A complete asset list helps coordinate logistics and guarantees nothing is left behind or mishandled during the move-out. For more in-depth strategies, our guide on IT asset management best practices provides further guidance.
How to Choose a Certified Recycling Partner in Atlanta
With a comprehensive IT inventory in hand, you’ve reached the most critical decision point: selecting the right ITAD vendor. This is not a logistical choice; it is a significant business decision. A legitimate, certified partner for Atlanta electronics recycling serves as your primary defense against data breaches and environmental liability. An uncertified operator, in contrast, can expose your company to catastrophic financial and legal consequences.
There's a vast difference between a true ITAD partner and a simple scrap hauler. One provides a secure, documented, and legally defensible process. The other simply makes your old equipment disappear, leaving your business holding all the liability with no proof of proper disposal. For any organization that takes data security and compliance seriously, this choice is non-negotiable.
Decoding the Certifications That Matter
When a vendor claims to be "certified," you must verify the specifics. In the electronics recycling industry, two certifications are recognized as the gold standard for security, environmental responsibility, and professional operations. Do not consider a partner that lacks these credentials.
Here’s what to look for:
- R2v3 (Responsible Recycling): This is the leading standard for the electronics recycling industry. An R2v3 certification signifies that the vendor has passed rigorous third-party audits covering data security protocols, environmental management systems, and worker health and safety. It is a comprehensive validation of professional operations.
- e-Stewards: Developed by the Basel Action Network, this certification is intensely focused on preventing the illegal export of hazardous e-waste to developing countries. It is widely regarded as one of the most stringent environmental standards in the industry.
A vendor holding one or both of these certifications has invested significant capital and resources to prove they operate correctly. It is your most reliable initial indicator that you are dealing with a professional firm, not an operator who might improperly dispose of your equipment—and your sensitive data.
Choosing a certified recycler is analogous to hiring a bonded and insured general contractor for a major facility renovation. It is your primary assurance that the job will be done correctly, safely, and in full compliance with industry best practices, effectively transferring the risk from your organization to theirs.
Beyond Certifications: What to Ask a Potential Partner
Certifications are the entry ticket, but they are only the beginning. A true ITAD partner should be able to answer detailed operational questions with confidence and transparency. Their responses will reveal everything about their security protocols and their ability to protect your business.
Before signing any agreement, obtain clear answers to these questions:
- Can you provide a complete, serialized chain of custody? This is non-negotiable. They must demonstrate the ability to track every single asset by serial number from the moment it leaves your facility until its final destruction or resale.
- What are your specific data destruction methods and standards? They should be able to detail their wiping (e.g., DoD 5220.22-M), degaussing, and shredding processes and confirm they provide a serialized Certificate of Destruction.
- How secure are your facilities? Ask for specifics: 24/7 video surveillance, controlled access points, and segregated, locked areas for storing data-bearing devices.
- Do you carry downstream vendor liability insurance? This is absolutely critical. This policy protects your organization if a data breach or environmental issue occurs with one of their recycling partners down the line.
Their confidence and transparency in answering these questions are key indicators. If a vendor becomes vague or defensive, consider it a major red flag and terminate the discussion.
Recognizing the Dangers of Uncertified Vendors
It can be tempting to engage an uncertified operator offering a low price, but the hidden costs are staggering. These companies invariably cut corners on security and compliance, leaving your business dangerously exposed to risk.
Consider this real-world scenario: An Atlanta-based healthcare provider hired a low-cost, uncertified "recycler" to dispose of old patient check-in kiosks. The vendor performed a basic wipe on the hard drives and resold the machines. Months later, patient data was discovered on those devices, triggering a massive HIPAA violation, six-figure fines, and a public relations crisis that severely damaged their reputation.
That is the exact risk you take with an unvetted partner. An R2v3 or e-Stewards certified company would have physically shredded those drives as a standard procedure. They would have provided a Certificate of Destruction that would have legally protected the healthcare provider. While there are many options for where to recycle electronics, selecting a certified business partner is the only way to properly manage corporate risk. The minimal cost savings upfront are never worth the astronomical price of a data breach.
Data Destruction Methods That Ensure Compliance
For any business, the data residing on retired IT assets represents a significant liability. Simply decommissioning a server or storing old laptops does not eliminate risk; it merely postpones it. A thorough understanding of data destruction methodologies is therefore non-negotiable for any organization managing Atlanta electronics recycling.
The appropriate method ensures that sensitive information is rendered permanently unrecoverable, shielding your company from costly breaches and regulatory penalties. It's about understanding the critical differences between wiping a drive and physically shredding it—this knowledge empowers you to have substantive, specific discussions with any ITAD vendor you evaluate.
Choosing Between Wiping, Degaussing, and Shredding
Not all data destruction methods are created equal. The optimal choice depends on the media type, your industry's compliance requirements, and your organization's internal risk tolerance. The ultimate objective is always the same: to make the data forensically unrecoverable.
Here are the three primary methods a certified partner will utilize:
- Data Wiping (Sanitization): This software-based approach overwrites existing data with random characters. A DoD 5220.22-M 3-pass wipe is a widely accepted standard, rendering a drive safe for reuse or resale in many commercial applications.
- Degaussing: This process uses a powerful magnet to destroy the magnetic field on older hard disk drives (HDDs) and tape media. It is exceptionally fast and effective for these specific media types but is completely ineffective on modern Solid-State Drives (SSDs).
- Physical Shredding: This is the definitive method of data destruction. The drive or other media is fed into an industrial shredder that reduces it to small, unsortable fragments. For regulated industries, this is not merely a best practice—it is a compliance mandate.
As you evaluate these options, remember that effective Compliance Liability Control requires a process that is both technically robust and legally defensible.
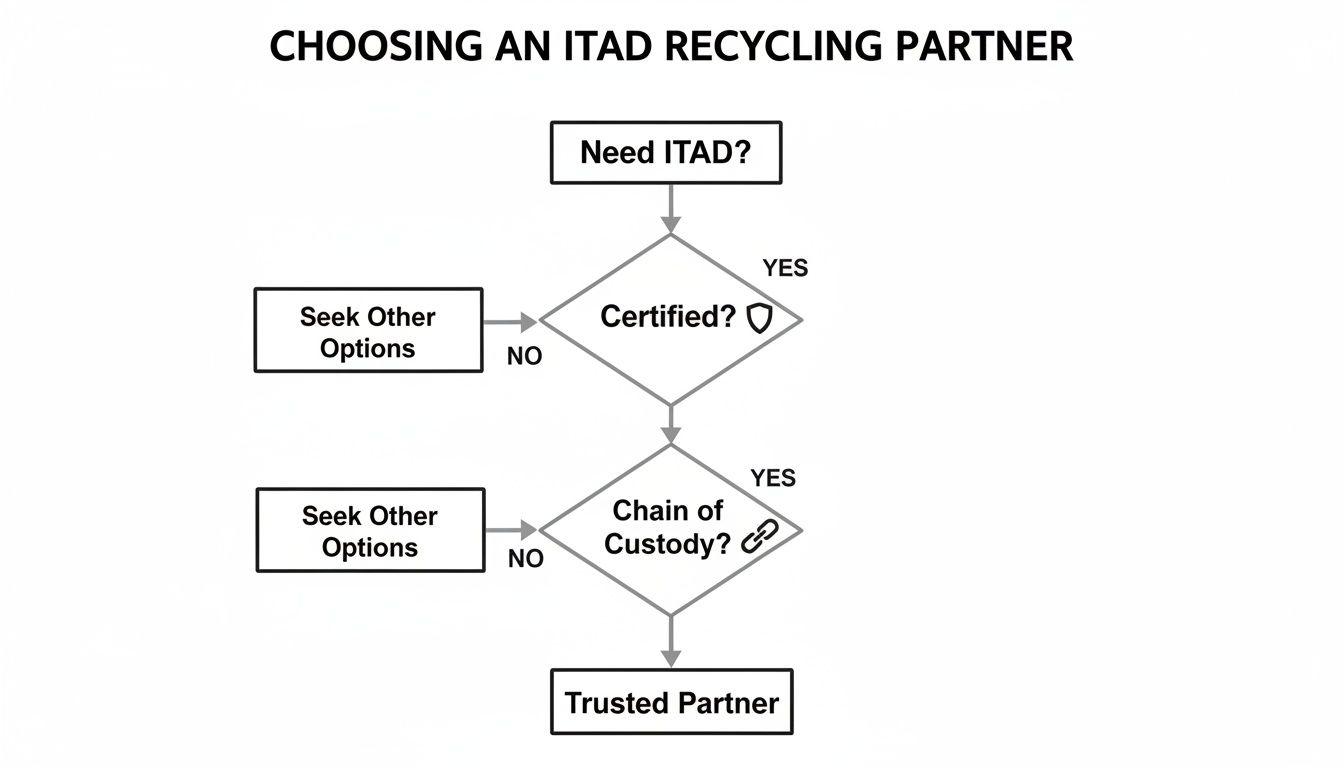
This decision tree provides a high-level overview of how to select the right partner for your Atlanta electronics recycling project, emphasizing critical checkpoints like certification and chain of custody.
As the chart illustrates, verifying certifications and securing the chain of custody are foundational steps that must be completed before discussing specific destruction methods.
When formulating a data destruction strategy, it is useful to compare the methods directly. Each has a specific role based on your security requirements and the type of hardware being retired.
Data Destruction Methods Compared
| Method | Process Overview | Security Level | Best For… | Compliance Alignment (HIPAA, etc.) |
|---|---|---|---|---|
| Data Wiping | Software overwrites drive sectors with random data, often in multiple passes. | High | Reusing or reselling assets; non-sensitive data; lease returns. | Sufficient for many standards, but may not meet the strictest requirements alone. |
| Degaussing | A powerful electromagnetic field erases the magnetic data on HDDs and tapes. | Very High | Rapidly destroying large volumes of magnetic media that will not be reused. | Excellent for magnetic media, but ineffective for SSDs, making it an incomplete solution. |
| Shredding | The physical device is ground into small, irreparable fragments. | Absolute | High-security needs; end-of-life SSDs; meeting strict HIPAA/FACTA/DoD compliance. | The gold standard for ensuring forensic data recovery is impossible. |
This table clarifies that while wiping is effective for preserving asset value, shredding is the only method that offers an absolute guarantee of destruction—a critical requirement for regulated industries.
When Physical Destruction Is Non-Negotiable
For many Atlanta businesses operating in healthcare, finance, or government contracting, data wiping is insufficient. When handling protected health information (PHI) under HIPAA or sensitive financial data under FACTA, physical destruction is the only acceptable method.
Consider a hospital retiring a batch of patient monitoring systems. Even if those drives are wiped, the potential risk associated with a single recoverable data fragment is unacceptably high. The only way to achieve full compliance is to physically shred every data-bearing device and obtain the documentation to prove it. This approach eliminates all doubt and creates an unimpeachable audit trail.
The question isn't just "Is the data gone?" For compliance purposes, the real question is, "Can I prove, with legally defensible documentation, that the data is physically impossible to recover?" Only physical shredding, documented by a serialized Certificate of Destruction, provides that absolute guarantee.
The Certificate of Destruction: Your Ultimate Legal Safeguard
Regardless of the method chosen, the process is not complete until you have the correct documentation. A serialized Certificate of Destruction (CoD) is the single most important document you will receive from your ITAD partner. It is not a mere receipt—it is your legal proof of compliance.
This document must list every asset by its serial number and confirm the exact date and method of destruction. In the event of an audit or legal inquiry, that CoD serves as your official record of due diligence. It effectively transfers liability from your organization to your certified vendor. Without it, you have no verifiable proof, leaving your business exposed to significant risk.
Learn more about our process for providing secure data destruction and the critical documentation that protects your business.
Planning a Seamless On-Site Pickup
You have completed the critical preparatory work of inventorying your assets and vetting a certified partner. Now comes the execution phase: the physical removal of your retired equipment. A professional pickup is not simply a truck arriving at your facility; it is a carefully coordinated operation designed for security, efficiency, and minimal disruption to your business operations.
The objective is to remove outdated technology from your premises without impeding your team's productivity or creating a security vulnerability. This is especially critical during a data center decommissioning, an office-wide technology refresh, or a full building cleanout. A smooth pickup ensures the secure chain of custody established at the outset remains unbroken all the way to the processing facility.
Coordinating the Logistics for a Smooth Operation
Success in this phase depends on clear communication and thorough preparation. Your ITAD partner should collaborate closely with your facilities manager or IT lead to map out the entire process in advance. This goes well beyond simply selecting a date and time.
The plan must address the specific logistical challenges of your location. Key details to coordinate with your vendor include:
- Access and Egress: Location of the loading dock, availability of freight elevators, and navigation of any narrow hallways or staircases.
- Scheduling for Minimal Disruption: Planning the pickup during off-peak hours, such as early morning, late afternoon, or a weekend, can prevent interference with your daily workflow.
- On-Site Team Roles: Designating a single point of contact from your staff to oversee the pickup and address any questions from the logistics crew is a best practice.
Finalizing these details beforehand prevents last-minute complications and ensures the vendor's team arrives fully prepared to execute the plan efficiently.
Preparing Your Site and Assets
On the day of the pickup, having your assets staged and ready is the most effective way to maintain momentum. While a full-service ITAD partner will handle the heavy lifting, some preparation on your end can make a significant difference. This can be as simple as consolidating all equipment into a single, secure, and easily accessible room.
Your vendor's team should arrive with all necessary equipment—dollies, pallet jacks, and secure, locked containers for data-bearing devices. Their process should be methodical and transparent. A key indicator of a secure process is the on-site shrink-wrapping and labeling of each pallet before it is loaded onto the truck. This practice prevents damage and asset commingling during transit.
A professional on-site pickup should operate with the precision of a well-rehearsed project. The team should secure and document assets efficiently while respecting your workspace and operational schedule.
The transport itself is the final step in the on-site chain of custody. A certified partner will always use secure, GPS-tracked vehicles. This provides a verifiable audit trail and peace of mind, confirming that your assets are monitored from the moment they leave your control.
For Atlanta businesses, these dedicated commercial services are essential. In 2023, while the city's municipal program collected nearly 20,000 tons of recyclables, the overall recycling rate was only 23%, far below the national average. These figures highlight why residential programs are inadequate for commercial needs, reinforcing the importance of specialized Atlanta electronics recycling services capable of handling secure, large-scale corporate projects.
Proper planning with a professional partner transforms a potentially chaotic cleanout into a controlled, secure, and efficient process. You can learn more about what to expect when you schedule an electronic recycling free pick up and how to prepare your facility.
Answering Your Atlanta Electronics Recycling Questions
When managing a commercial electronics recycling project, numerous practical questions arise. IT managers, compliance officers, and business owners require direct answers to make informed decisions. We've compiled the most common inquiries from businesses here in Atlanta to provide clarity.
What Is the Real Cost of Business Electronics Recycling?
The honest answer is: it depends. The final cost is determined by the volume and type of equipment, logistical factors such as elevator access, and the specific data destruction services required. However, the service is often more affordable than businesses anticipate.
For example, basic data wiping may be included in the service, with primary costs related to secure transport and the physical shredding of hard drives. Certain legacy items, like CRT monitors, incur separate fees due to hazardous waste handling requirements. The most accurate way to determine cost is to request a custom quote based on your detailed inventory.
When you compare this expense to the potential multi-million dollar cost of a data breach or compliance fine, professional ITAD services are clearly not a cost center, but rather a critical investment in risk management.
Is a Certificate of Destruction Truly Necessary for Our Business?
Yes, absolutely. A serialized Certificate of Destruction (CoD) is not just paperwork—it is your legal, auditable proof that your company’s sensitive data was securely and permanently destroyed. This document is essential for demonstrating compliance with regulations like HIPAA and FACTA.
In the event of an audit, the CoD serves as your verifiable evidence of due diligence. It formally transfers the liability for the data from your organization to your certified partner. Without it, you have no defensible position, leaving your business exposed to significant legal and financial repercussions.
Think of a Certificate of Destruction as the final, legally-binding link in your chain of custody. It is the document that proves you have a serialized, third-party guarantee that your data is irrecoverable.
Is Our Project Too Small for a Professional ITAD Service?
Not at all. Professional ITAD companies in Atlanta serve businesses of all sizes, from small enterprises to Fortune 500 corporations. A reputable partner provides the exact same level of security, documentation, and professionalism whether you have two pallets of equipment or an entire data center to decommission.
The core principles of secure data handling and certified recycling are not scalable; they are absolute. They are either followed or they are not. The best first step, regardless of your project's size, is to contact a provider with your inventory list to discuss your needs and develop a clear plan.
Can’t Our Internal IT Team Just Wipe the Drives?
While an internal wipe is a good preliminary step, it is not a substitute for certified, third-party data destruction. Professional vendors use audited, validated software and processes that guarantee data is forensically unrecoverable. Critically, they provide the official Certificate of Destruction required for your compliance records.
It is this independent, third-party verification that withstands scrutiny during an audit and protects your business from liability. Relying solely on an internal process creates a significant gap in your compliance and risk management strategy—a gap you do not want to be forced to explain later.
Ready to secure your retired IT assets and ensure compliance? Contact Atlanta Computer Recycling today for a transparent, no-obligation quote tailored to your specific needs. Visit us at https://atlantacomputerrecycling.com to get started.